Part 2: OMG! Not another digital transformation article! Is it about the evolution from RIM to Content Services?

Abstract
Humans have used technology to transform their societies from prehistoric times up to the present. Society begrudgingly accepted the transformative changes, yet the changes moved society forward. Now information technologies and the information revolution are again transforming society. The COVID-19 pandemic further accelerated the transformation from many years to just a couple of years. This 3-part series will discuss digital transformation (DT) from several perspectives. Part 1 discussed the key DT business drivers, concepts, and technology trends, how they are transforming organizations and society, and how they are affecting business users and customers. Some technology trends such as real-time data analytics are on-going, while others are more recent, such as blockchain.
Here, Part 2 discusses the critical factors for a successful DT journey, because organizations need to do a “mind-shift” from traditional records and information management (RIM) practices to content services (CS). This means imagining the “art of the possible” for a new future using a cloud computing model to deliver transformative change. This includes defining the product scope of the DT journey and the digital products and services that will deliver transformative change for a new future.
Part 3 will discuss how to manage the various DT risks. One essential step is developing the DT business case and connecting it with the critical success factors (CSFs) and the product scope. This discussion will include methods, tools, and techniques such as using personae and identifying use cases that have high business value, while minimizing project risks. This part will also discuss managing CS risks such as ransomware, privacy, change management, and user adoption. Finally, Part 3 will look to the future, will present next steps, and will discuss key takeaways.
Introduction
Part 1 of this 3-part series discussed DT by examining and discussing concepts and trends. These trends have “moved the needle” from traditional records and information management (RIM) practices to CS.
What are traditional RIM practices? ARMA (2017) describes RIM practices as the “knowledge and skills required to systematically manage information assets from creation or receipt through processing, distributing, sharing, using, accessing, organizing, storing and retrieving, and disposing of them. Information is a vital organizational asset, and organizations depend on accurate, complete, and readily available information to assist in decision-making; providing litigation support; improving organizational efficiency; documenting compliance with legislative, regulatory, contractual, and audit requirements; and providing historical reference” (p 4).
While these RIM practices are still important to help ensure governance, compliance, and manage risks, it is also important to realize that information is both a product and a service. So, information must be readily available to automated systems and business users and customers as a product or a service.
Enabling CS for DT
Business users and customers expect products and services on their terms and on demand. Ordering food from an app, downloading a movie while in a car – all of it, anytime, anywhere, on any device! Not meeting this expectation may lead to negative posts on social media – anytime, anywhere, and from any device.
This “anytime, anywhere” aspect is possible by merging traditional RIM practices of document and records lifecycle management and DT, but with a focus on how to “package” the content to deliver a product or service.
Understanding the changing requirements and business value of the information, from creation / receipt to eventual disposition from the perspective of RIM and DT, is essential for CS because business value is in the content, and because of compliance requirements. For example, once a health record has met the regulatory requirements, the record can be anonymized and kept for years for such purposes as medical research and predictive analytics. Another example is when sensitive information is removed from transaction data after meeting operational requirements, but the data is kept for analytical processing such as market research and trend analysis.
The “Art of the Possible” for the End-state
The “Art of the Possible”[1] is a song in Evita, by Andrew Lloyd Webber and Tim Rice. The opening lyrics are “One has no rules / Is not precise.” These lyrics are strangely appropriate because they reimagine a future that is not constrained by rules or by the need to be specific. Similarly, the DT journey is about reimagining the future – and imagining new ways of doing things. See Table 1 listing some common examples of the “art of the possible.
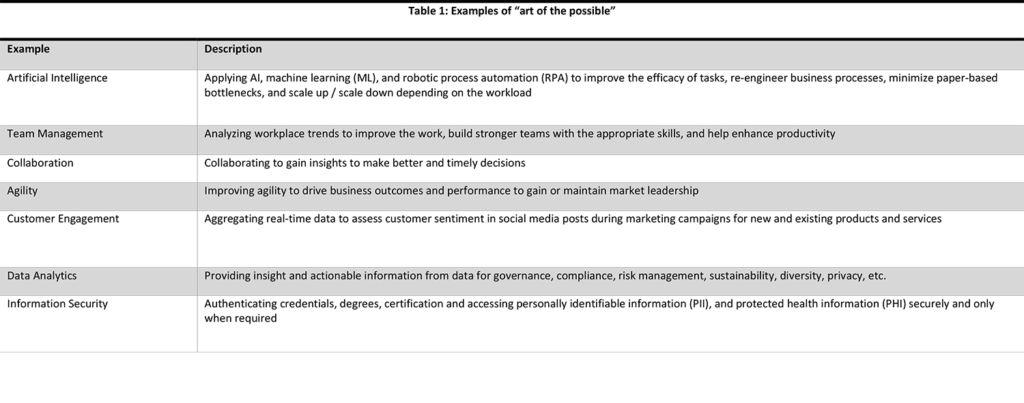
Many DT journeys fail because the strategies do not properly assess the stakeholders’ needs and the organization’s capabilities. As well, the organization’s management is not committed to adopting new digital processes and technologies. Therefore, the response is half-hearted at best.
The DT journey requires a new strategy and roadmap instead of tweaking old ones. This can be a challenging “mind-shift” for many organizations under normal operating conditions. However, the pandemic changed normal operation conditions and compressed several years of DT and technology adoption into less than one year! The pandemic forced every organization to think about the “art of the possible.” Thus, an organization needs to constantly ask what it can do differently that others are not doing to disrupt the future and seize the opportunity for leadership in the fast-changing digital economy. In fact, organizations should expect to face constant disruption, to adapt continuously, and to transform constantly; otherwise, they will face an uncertain and risky future.
The First Revolution Meets the Fourth Revolution
In the Neolithic Revolution, early humans discovered agriculture, which helped establish early civilizations. Over the millennia, agriculture has used countless technologies to increase production. Now the Fourth Industrial Revolution[2] is “digitizing the farm”— that is, radically reimagining agriculture through big data analytics that help farmers increase crop yields and using artificial intelligence (AI) to monitor pests, plant diseases, soil nutrients, and other growing conditions. Using “digital farming” techniques such as moisture sensors in the soil and regular and infrared cameras on drones, the Internet of Things (IoT) can capture images nonstop and transmit them to a central location for processing. AI can analyze this vast amount of data from many sensors and combine it with other sources such as weather forecasts and historical data to recommend options for action. For example, the farmer can decide where to increase or decrease irrigation, when and where to apply herbicide, and more. Even better, the automated systems can perform the actions and inform the farmer! The farmer can use AI to evaluate the results and then, based on data, decide to repeat or modify the process.
The travel industry has already reimagined its future. Before, travellers booked their trips through agents, who issued paper tickets, confirmations, car-rental documents, and so on. In 2004, Giovanni Bisignani, CEO of the International Air Transport Association (IATA), made the case for the travel industry to reimagine its future: “Internet savvy travelers appreciate the convenience … Our mission is to keep the value and eliminate the cost. Look at the success of the low fare sector. Starting with a clean sheet of paper, they have designed business processes that are streamlined. Passengers benefited with low fares. Importantly, the airlines and their shareholders are realising profits” (Bisignani, 2004). Since then, travellers have mostly bypassed the travel agent. There is virtually no paper today. Booking online and getting e-tickets and confirmations on a smart phone are normal.
The pandemic is forcing every industry and every organization to reimagine their future. How will organizations use so-called “vaccine passports” related to employees and customers and how will organizations secure their protected health information (PHI) in response to changing health directives? PHI and “vaccine passports” might be required and be operationally important for contact tracing.
Another example, mentioned in Part 1, is that of auction houses, which are reimagining their future by using nonfungible tokens (NFTs) and blockchain technology. The high-end auction business in rare paintings and other collectibles is known for catering to millionaires. This rarefied client base is changing, as the nouveau riche become comfortable buying NFTs for digital art and collectibles and paying with cryptocurrencies (Thaddeus-Johns 2021, Tarmy 2021). Time will tell what impact this trend will have, to what extent it will disrupt the auction business, and how auction houses will reimagine their future using DT. One thing is certain: digital art is here to stay.
Critical Success Factors (CSF)
Part 1 discussed many DT technology and non-technology trends and concepts, and some of these can be considered CSFs. Below are the CSFs that can influence the DT journey to a successful conclusion.
- Cloud Enablement
This is a “mind-shift” to leverage cloud-first capabilities, tools, and to deploy services that are outside the firewall. Implied herein is a cloud computing model that ARMA (2016) defines as “A model for enabling ubiquitous, convenient, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, storage, applications, and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction” (p 9). Leveraging a cloud-first approach also allows organizations to deliver new market-leading solutions more expediently.
Delivering solutions expediently is critical in order to respond quickly to changing demand and market trends. The cloud enabled computing model allows the organization to scale up during peak periods such as new product launches and holiday shopping, and then scale down after the event. Thus, computing resources are available on-demand at any time.
- Intelligent Capture
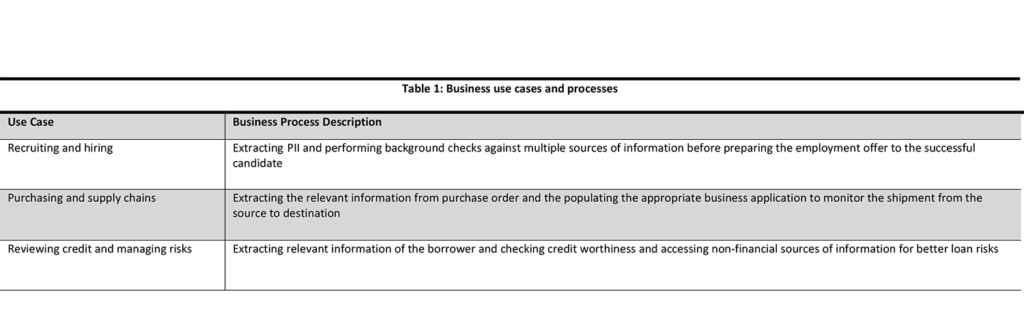
Capturing content focuses on opportunities to convert physical information into digital formats across multiple channels and sources. Intelligent capture can also leverage capabilities of robotic process automation (RPA) using AI via machine learning (ML) and machine teaching (MT). Analytics using RPA can examine, analyze, and identify unstructured content and auto-classify data based on rules learned by the AI engine. Thus, intelligent capture is used across any number of business use cases and supporting processes. See Table 2 for a few examples.
Initiatives for scanning and digitizing physical content started in the late 1980s. In the 2000s, these projects became significant initiatives, and most organizations thought this was the extent of DT – “Scan the documents and output them to disk, then we’re done!” This process was called Computer Output to Laser Disk (COLD). COLD is a “technology that records and then stores computer-generated data onto optical disks for online access” (ARMA 2016, p 10). COLD technologies are also referred to as enterprise report management (ERM), “A system that transforms reports into documents and data that can be searched, accessed, and leveraged in business processes” (ARMA 2016, p 19). Some organizations went further and stored the scanned digital files in an EDRMS repository to improve RIM capability; these organizations were “moving the needle.”
Intelligent capture also includes converting physical formats such as microfilm, microfiche, film roles, negatives, x-rays, and cassettes into digital formats and auto-classifying the content. Today, scanning and digitizing are still significant initiatives because of the large volume of physical records that organizations have in storage. Unfortunately, some organizations continue to think this is their DT journey, because this traditional RIM activity is their “imagined” end stated.
- Repository Neutral Content
Almost all organizations have multiple storage repositories with digital information, usually locked into legacy systems and platforms, and they are proprietary. So, accessing the content is not easy. On the other hand, neutral repositories are storage locations that are independent of the underlying systems and technology creating content. Thus, the content is available using diverse tools. Integrated collaboration leverages diverse technology platforms and disparate repositories to allow teams to save, search, and share content. This can include knowledge management, data analytics, data management, and more. As well, repository neutral content can quickly be delivered via customer data platforms (CDP), managed via digital asset management (DAM), and monetized via digital rights management (DRM) systems using DevOps. Finally, Content as a Service (CaaS) , Managed Content as a Service (MCaaS), and other cloud services critically depend on repository neutral content that can be accessed from any device.
- Integrated Collaboration
Integrated collaboration is closely related to repository neutral content because collaboration should be possible on any device regardless of where the content is stored. Consider the scenario in which one team member is authoring a document on a Windows laptop, while another is co-authoring on an Android tablet, while a third is using an electronic whiteboard with touch screen and stylus pen to provide feedback in real-time. After saving the document, a fourth employee might open the document on a Mac to review and approve it. In a world that’s increasingly digital, the underlying platform and repository do not impede collaboration. In this scenario, integrated collaboration leverages diverse technology platforms and disparate repositories to allow teams to save, search, and share content.
- Information Governance (IG)
IG is a very critical, if not the most significant, CSF for a DT initiative. It is acknowledged that IG “helps organizations achieve business objectives, facilitates compliance with external requirements, and minimizes risk posed by sub-standard information handling practices” (ARMA 2016, p 28). Therefore, establishing an IG committee of senior managers is essential for DT because it will affect the entire organization[3].
Discussions of IG often lead to a discussion of data governance (DG) and whether the two are different. One argument is that DG focuses on structured data in databases, while IG is about unstructured content. While this is certainly true, the data can be used to create unstructured content such as reports, audit logs, dashboards, and so on. On the other hand, intelligent capture using RPA can convert unstructured content into structured content by inputting the data into a database. Thus, an argument can be made that IG and DG are two sides of the same coin. Therefore, the position of this article is that IG includes DG because information is data in context. Then, the information is assessed based on experience and insight leading to action. In turn, this action generates new data, and the cycle repeats (see Part 1).
- Content Services
This is recognized as another key CSF because it facilitates the capacity to deliver products and services on-demand to any device, anywhere, at any time, independent of the content repository. This is possible using CaaS / MCaaS along with supporting technologies such as CSP and DRM.
In many cases, this is the end goal of a successful DT initiative. Since the content has business value, then IG, compliance, security, and privacy are critical considerations when delivering it to business users and customers as a new product or service. More importantly, the success or failure of a new product or service can determine the success or failure of a DT initiative. The DT initiative needs to define the product scope. The Project Management Institute (PMI 2017, p 715) defines product scope as “The features and functions that characterize a product, services, or result.”
Therefore, the business case needs to clearly articulate the product, service, or result of the DT initiative – i.e., “What is the end-state?” In fact, the business case should identify the benefits and outcomes from the perspective of different stakeholders. It is important to understand the end-state because identifying the appropriate technology will be necessary in order to deliver the content on-demand to any device, anywhere, and at any time.
Part 1 stated that data is the “fuel” behind DT. If so, then CS “drives” DT. What does this mean? It means CS retrieves data from any number of sources, then transforms it in a given context and delivers the content in a format that humans and other systems can consume. Real-time stock prices, traffic updates, weather and temperature data, alerts for hotel and airline ticket prices, and alerts for online shopping are just a few examples of CS delivered to devices like smart phones, tablets, and laptops. As stated above, this is usually the end goal of a successful DT initiative.
- Auto-classification
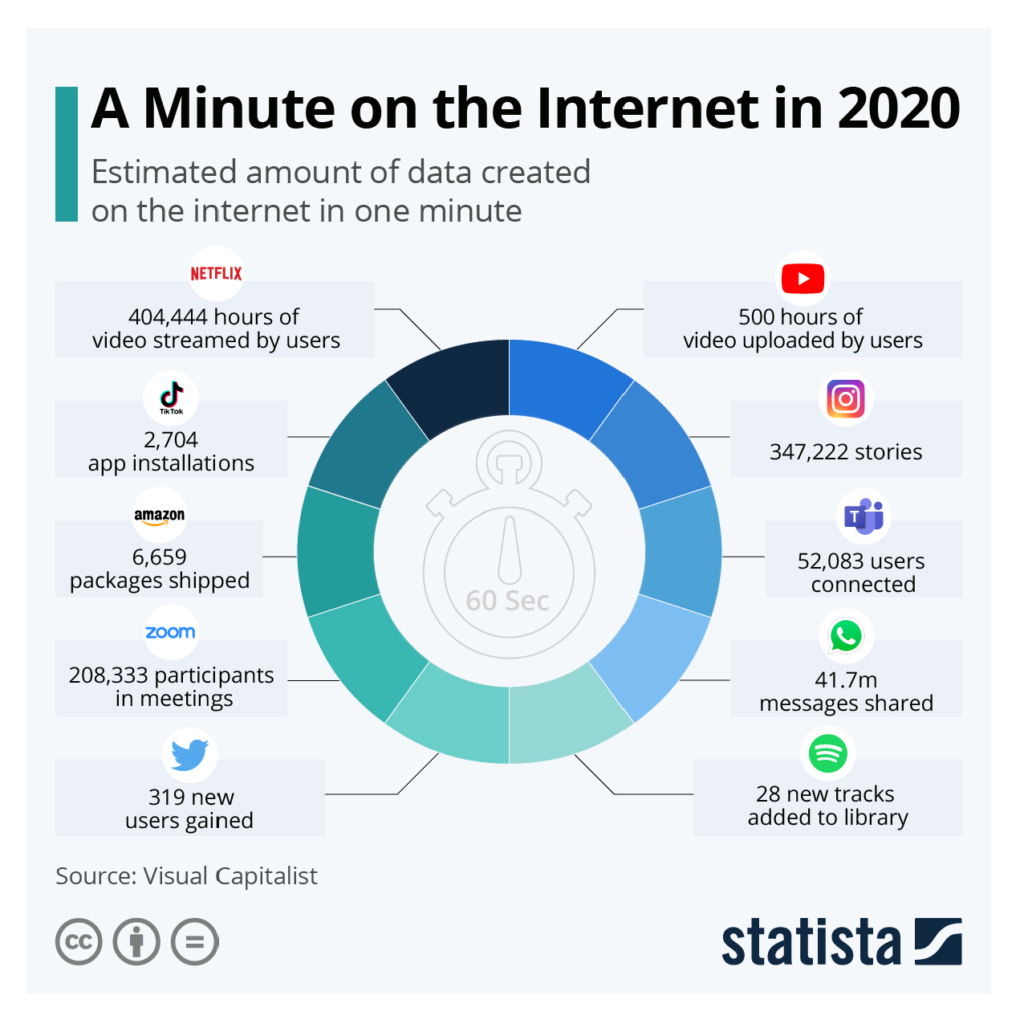
Reviewing and classifying content according to a specific taxonomy has always been a manual effort. Today, it is not possible to review all the content created in an organization. While a lot of content created on the internet might not be a record, the content still needs to be classified for indexing and searching. How else will someone find images of dogs, cats, teddy bears, and all the rest? (See Figure 1 [Jenik 2020]). Someone or something has to classify the content. That “something” is AI. Thus, auto-classification tools are the only solution to systematically identify and classify content into categories according to a taxonomy representing logical structures such as functions, activities, procedures, and methods. Within organizations, business users are creating vast amounts of content and duplicating it in various spots, such as shared devices and online repositories. This information also needs to be auto-classified. Auto-classification can leverage AI using RPA and ML / MT to analyze the digital content and categorize it, including redundant, obsolete, and temporary (ROT)[4] content. Much of the content will never be accessed, yet the cost to manage ROT content will continue to increase.
IoT devices are another source of content that must be auto-classified because much of this content might be mission-critical, personal, and / or sensitive. “More and more, information is generated by equipment, intelligent devices, or other systems. Although not generated by humans, this can be mission-critical data” (ARMA 2018, p 68). IoT sensors attached to machinery can be time sensitive and operationally important for workplace health and safety compliance. Consider sensors attached to factory equipment that monitor for performance and scheduling repairs. Process control of equipment and large industrial plants has evolved over time from control panels in machinery to sensors that use wireless transmission to feed the data to a central location for processing. Then, based on the data, past repair information, and other historical information, AI can predict and schedule the next maintenance period.
- Customer Experience (CX)
In the age of DT, organizations must ensure memorable experiences for their customers. They must look at the value of experiences across a range of products and services to increase brand recognition, customer loyalty, market share, business performance, and more.
CX is the collection of experiences, emotions, expectations, and impressions resulting from interactions with online services and digital products across all platforms and delivery channels from an organization’s website, mobile apps, chat services, and call centers. CX is closely associated with CS because from an existential perspective a thumbs up or down on social media can affect their success. For example, on e-commerce and social media sites, a positive CX will help foster “stickiness” that drives social engagement and sales – or “social commerce.”
Consider the use case of the CX of fans, i.e., the fan experience. This is very important in sports because during winning or losing seasons the die-hard fans can help the team break even (notwithstanding revenue sharing from broadcast rights, corporate sponsorships, and so on). In fact, many sport franchises, leagues, celebrities, fashion designers, and artists are at the forefront of using DT to connect with their fans, from special previews for members-only fan clubs to fan appreciation events with sport stars, and more. For example, a personal endorsement from a celebrity can drive customers to try new products and services that can drive “social commerce.” Despite the pandemic, artists can live-stream their shows using streaming apps to connect with fans and earn money at the same time. Celebrities are critical to the fan experience, and DT has changed the fan experience.
- Employee Experience (EX)
DT provides organizations the opportunity to improve the employee experience as well. Gartner (2021) defines EX as “the way in which employees internalize and interpret the interactions they have with their organization, as well as the context that underlies those interactions.”
An organization’s processes, policies, and technologies must be employee-centric to optimize the employee experience. “Today’s employees are consumers of content in the workplace. They expect a personalized digital experience and the ability to connect with information through consumer-like technology platforms that are as convenient as the ones they use outside work. The organizations that treat their employees like premium customers, from the recruiting process through the alumni experience, are best positioned to retain talent and see the highest performance in return” (HBR 2020, p 1).
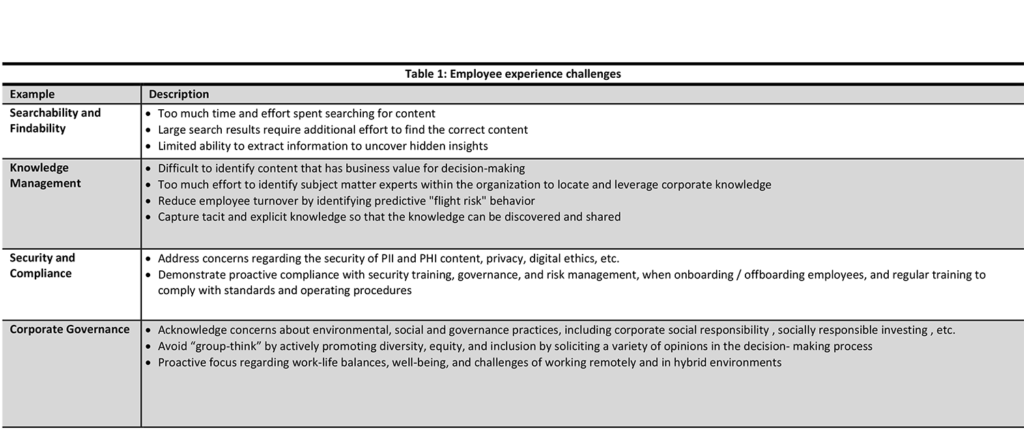
There are many internal challenges that can impede the EX. Some examples are listed in Table 3: Employee experience challenges. The shift to working remotely has further exacerbated the EX challenges to build connections necessary for productive team dynamics. Without the right tools, policies, and processes, the employees’ engagement can suffer and can materially affect the organization’s performance. “More than 90% of executives … who say their organizations make EX high priority report that their team have the tools and technology to do their work efficiently, compared with 76% of all the other respondents” (HBR 2020, p 1).
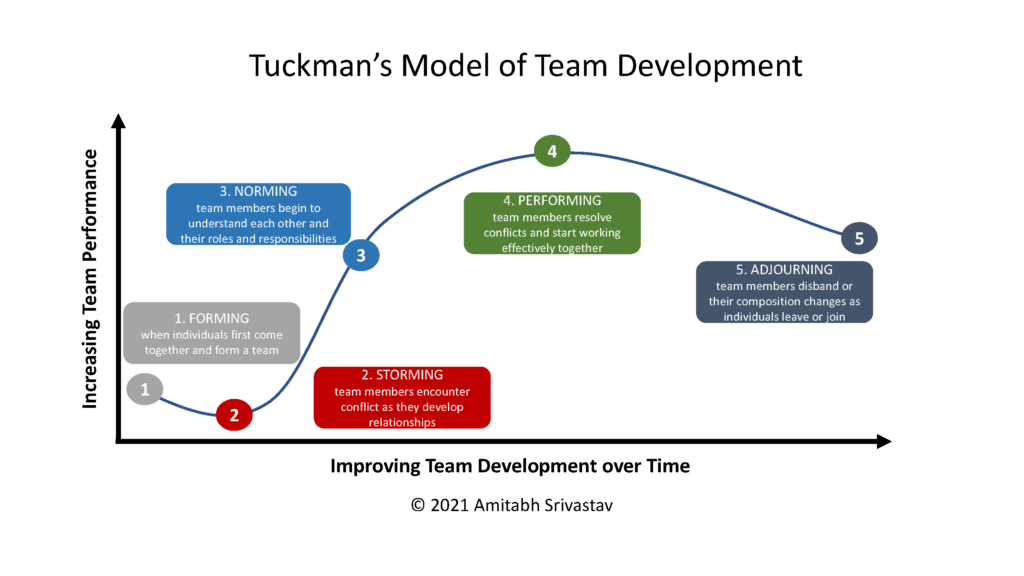
It can be a challenge to get remote employees “to gel” and have a sense of buy-in in the new, hybrid work environments. There are many team development models that can help improve EX (ARMA 2018, p 121). One is by Bruce Tuckman, who identified five stages within a traditional group’s development life cycle (Tuckman 1965, Tuckman et al. 1997). This model can apply to the EX for teams either on-site or working remotely. Figure 2 illustrates the five stages.
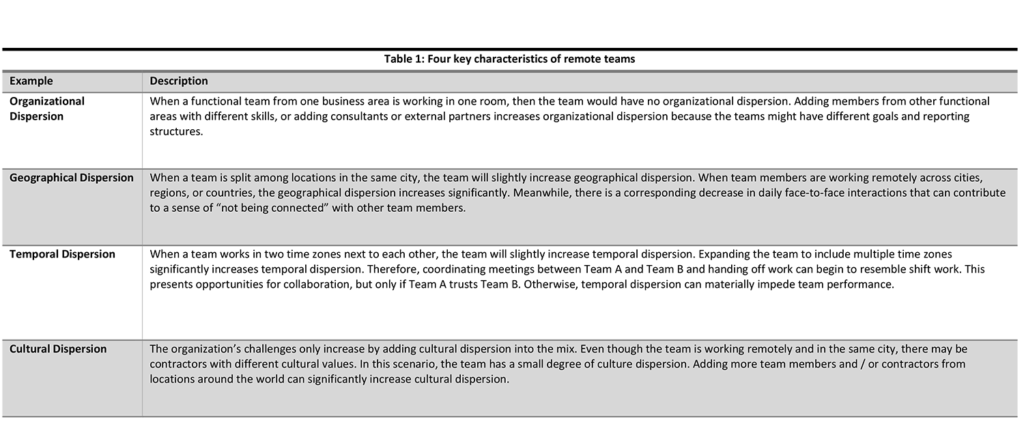
Furthermore, remote teams have four key characteristics that can also affect their development (Srivastav 2014, p 37), as listed in Table 4.
DT Scope
While the CSF concepts discussed above help define a DT initiative, it still needs to define the product scope of the DT initiative. So, what products and services will the DT initiative deliver to customers and / or employees, and how will DT deliver those products and services?
The scope for CS can be just as broad as the DT initiative itself. When the organization accepts a cloud-first strategy of a cloud computing service model, it includes the services previously mentioned – Infrastructure as a Service (IaaS), Platform as a Service (PaaS), Software as a Service (SaaS), Data as a Service (DaaS), Blockchain as a Service (BaaS), and Artificial Intelligence as a Service (AIaaS) from third-party cloud-based providers. This means that the business has to digitize the content creation and usage processes throughout the information lifecycle.
So, what might the DT’s product scope include?[5] The scope can include some of the following products and services.
- Information Architecture (IA)
IA overlaps many areas of design, such as navigation, user experience, user interface, security model, taxonomy, and metadata. A good IA is intuitive and represents how teams work within their business area, collaborate with other business areas, produce reports for management and oversight, and manage projects and initiatives. As well, the IA design needs to consider a taxonomy for RIM to store operational and vital records and demonstrate regulatory compliance.
- Records Management
RIM has traditionally focused on physical records management, but now the greater emphasis is on digital content such as documents, presentations, reports, websites, social media posts, chats, email, video conference, and multi-media. Access to the records should be on any device, from anywhere, anytime. RIM can include archival storage for long-term preservation and archival services.
- Document Management (DM)
In the past, DM mostly focused on “save, search, and share,” version control, metadata, and permissions. While those are still important, now DM also includes collaboration using real-time co-authoring, auto-classification of documents using RPA, document analysis to extract metadata using ML, and more.
- Artificial Intelligence
AI can perform data analytics on content from many sources and may focus on trend analysis, predictive analytics, modeling, and so on. AI can also identify trending topics, curate content from disparate repositories, and deliver it based on user-defined rules. Using the rules in conjunction with the IA design, the AI can auto-classify the content.
- Knowledge Management (KM)
KM is the collective and accumulated wisdom that organizations can use to gain insights. This is more critical than ever due to the exponential growth in content creation. While the focus is on digital content, it can also be non-digital content and includes the information in employees’ heads. An important source of organizational knowledge is either explicit knowledge or tacit knowledge. Explicit knowledge is already classified and is available in a knowledge base, blog, wiki, etc. The information can be searched and shared. On the other hand, tacit knowledge is in the business users’ heads – more specifically inside subject matter experts’ (SMEs) heads. The challenge is to convert the tacit knowledge into explicit knowledge. “Organizations with successful knowledge sharing cultures focus more on removing barriers to information flow … [so it is] … more dynamic, less static” (AIIM 2019, p 49).
All of this content needs to be classified so that it is searchable and findable. Only then can KM help uncover insight, drive innovation, improve organizational performance, reduce operational risks, increase market share, identify market trends, and exploit new opportunities. Lew Platt, Hewlett-Packard’s CEO in the 1990s, once famously stated, “If only HP knew what HP knows, we would be three times more productive” (Murray 2002). Which means that retaining, maintaining, and accessing organizational knowledge can be a key strategic differentiator. So, KM involves two critical activities – capture and categorize explicit and tacit knowledge, then disseminate it so the knowledge can re-used. While applications may come and go, data is enduring and empowering – and data “fuels” DT!
- Search Experience
Search applications can be “plugged” into content repositories and configured. The search technology needs to crawl the content on a regular basis and update a searchable index. It also must process queries to locate content matching the search criteria, and sort or rank the results based on filters. Finally, the search technology must format the results and render them for the user’s device.
Searching can be done within the application, such as in an EDRMS, or it can be enterprise-wide by searching other websites, directories, and databases to build a searchable index and to process queries. There must also be security measures to ensure that PII, PHI, and other sensitive information are only accessible to authorized business users.
- e-Discovery
This is closely related to the search experience and KM, but the focus is on discovering content in order to respond to litigation, compliance, investigation, and information requests. An important consideration for e-Discovery is the security model for who or which team will have privileges to see the content. Whoever is performing the e-Discovery will need read access to examine content that might be considered sensitive. This level of access is usually not granted under normal business operations. Therefore, the e-discovery solution needs careful consideration, due diligence, and consultation with legal counsel and other stakeholders and SMEs. Note that these statements should not be considered as legal advice.
- Digital Asset Management
Thinking of content as an asset is a “mind-shift.” This includes treating and managing content as business assets, applying a value to the assets, and perhaps monetizing them. DAM applies to such content as podcasts, videos, architectural and design documents, intellectual property, logos, trademarks, copyrights, and more.
- Digital Rights Management
If the digital asset has business value, then the organization has to manage and control access to it. DRM is a “form of managing digital content to limit access from a specific device and / or prevent unauthorized copying or conversion” (ARMA 2016, p 15). Content management tools would play a key role using SaaS, CaaS, MCaaS, and DaaS in a cloud-first strategy.
- Archival Services
Archival services should be viewed as a combination of KM, DAM, and DRM for organizations to develop and deliver new services and products. In some cases, DT is also an opportunity for organizations to monetize their archived audio, video, and other types of content libraries. Unfortunately, archival services are often an overlooked component of DT. Therefore, working with stakeholders is critical in order to understand how archival services can improve KM, DAM, and DRM. On the other hand, archival services can help manage the risks due to growing regulatory requirements, increasing enforcement actions, and changing market conditions by using e-Discovery, KM, and DAM solutions.
- Data Management
Data management has traditionally focused on structured data in warehouses and data marts, which have clean, structured data used for business intelligence, key performance indicators, decision modeling, and other analytics. Data lakes are the opposite; they are “full of stuff” from disparate sources of “raw data” that is mostly unstructured and lacking metadata. The Customer Data Platform Institute defines a data lake as “a collection of data copied from company systems, stored in its original forms and accessible for analysis and further processing” (CDP 2021).
The information explosion is challenging organizations to manage their data across multiple content repositories and have visibility into their digital assets. Vast amounts of data are stored in data lakes. Thus, they present interesting opportunities because information retrieval from a data lake is “fishing for information” that is relevant for the query, but not knowing where to look. So, extraction is critical to “mining out” very specific information from a particular data structure. This is where business users need to apply AI and ML along with complex statistical analysis tools to extract the specific information that is relevant for the query. Managing this data and content to derive knowledge and actionable insight involves both data management and KM. Therefore, the two are “connected” when dealing with large volumes of structured and unstructured data.
As mentioned in Part 1, good data management practices align with good RIM practices such as retention and disposition of structured data, secure storage of sensitive and personal information, long-term preservation of data and information. Data management is also part of good DG, which in turn is part of IG. Both IG and DG are important governance goals. For example, an organization can store and use many years of sales data for trend analysis, but can anonymize the data a year after the transaction. This supports good records management and privacy by removing personal information after it serves no business need, but keeping sales information for long-term trend analysis. The trend analysis can help the organization to anticipate market changes and to respond quickly to them by extracting and transforming the sales data, but still observe good IG and DG practices.
Looking Ahead to Part 3
DT is about reimaging the future by moving the organization from tradition RIM practices to delivering content as new products and services to business users and customers based a cloud computing model. A successful DT journey hinges on understanding critical success factors and defining the product scope. Part 3 will discuss the risks of the DT, and how to manage the risks using methods, tools, and techniques for developing the business case, delivering CS, improving the user’s experience, and assessing change management risks.
Reference:
- AIIM. (2019). The Official CIP Study Guide, AIIM.
- ARMA. (2016). Glossary of Records Management and Information Governance Terms, 5th ed., ARMA International TR 22-2016, ARMA International.
- ARMA. (2017). Records and Information Management Core Competencies 2nd ed., ARMA International.
- ARMA. (2018). Information Governance Body of Knowledge (iGBoK), 1st ed., ARMA International.
- Bisignani, Giovanni. (2004). Remarks of Giovanni Bisignani at the 2004 Simplifying the Business conference in Geneva, International Air Transport Association (IATA). https://www.iata.org/en/pressroom/speeches/2004-11-16-01. Retrieved April 2021.
- Bismarck, Otto von. (1867). Otto von Bismarck Quotes. BrainyQuote.com.https://www.brainyquote.com/quotes/otto_von_bismarck_398827. Retrieved April 2021.
- CDP. (2021). Customer Data Platform Basics, Customer Data Platform Institute. https://www.cdpinstitute.org/cdp-basics. Retrieved April 2021.
- Gartner. (2021). Gartner Glossary, https://www.gartner.com/en/information-technology/glossary. Retrieved March 2021.
- HBR. (2020). Pulse Survey: Making Technology an Integral Part of Your Employee Experience Strategy, Harvard Business Review Analytical Services, Harvard Business Review Business School Publishing. https://hbr.org/resources/pdfs/comm/salesforce/MakingTechnologyAnIntegralPartOfYourEmployeeExperienceStrategy.pdf. Retrieved May 2021.
- Jenik, Claire. (2020). Internet Activity: A Minute on the Internet in 2020, Statista, September 21, 2020. https://www.statista.com/chart/17518/datacreated-in-an-internet-minute/. Retrieved March 2021).
- Murray, Peter. (2002). Knowledge Management as a Sustained Competitive Advantage, Ivey Business Journal, March / April 2002. Ivey Business School Foundation, Western University, https://iveybusinessjournal.com/publication/knowledge-management-as-a-sustained-competitive-advantage/. Retrieved May 2021.
- PMI. (2017). A Guide to the Project Management Body of Knowledge (PMBOK® Guide), 6th ed., Newton Square, PA, Project Management Institute.
- Srivastav, Amitabh. (2014). Risk Management and Virtual Teams: An Exploratory Empirical Investigation of Relationships between Perceived Trust and the Perceived Risk of Using Virtual Project Teams. Thesis in Project Management, Université du Québec en Outaouais, 2014. Abstract available at http://di.uqo.ca/id/eprint/719.
- Tarmy, James. (2021). Money Isn’t the Only Reason Auction Houses Are Jumping On NFTs, Bloomberg, https://www.bloomberg.com/news/articles/2021-04-06/money-isn-t-the-only-reason-auction-houses-are-jumping-on-nfts. Retrieved April 2021.
- Thaddeus-Johns, Josie. (2021). What Are NFTs, Anyway? One Just Sold for $69 Million, The New York Times, https://www.nytimes.com/2021/03/11/arts/design/what-is-an-nft.html. Retrieved April 2021.
- Tuckman, B. W. (1965). Development sequence in small groups. Psychological Bulletin, 63(6), 384-399.
- Tuckman, Bruce. W., & Jensen, Mary Ann. A. C.(1997). Stages of small group development revisited. Group & Organization Studies, 2(4), 419-427.
[1] The actual quote for this cliché is “Politics is the art of the possible” by Otto van Bismarck (Bismarck 1867).
[2] The First Industrial Revolution started in mid-18th century. The Second Industrial Revolution started in the late 19th century. The Information Revolution of the late 20th century is considered the Third Industrial Revolution.
[3] Refer to ARMA’s many publications that discuss the importance of IG.
[4] Obsolete can also include outdated content, while temporary can also include trivial and transient content.
[5] Product scope is different than project scope. PMI (2017, p 717) defines project scope as “The work performed to deliver a product, service, or result with the specified features and functions.”
About the Author

- Amitabh Srivastav has deep knowledge of IG/IM and is a transformation strategist with over 25 years of PM experience. He has a strong portfolio of qualifications in strategy, transformation, and risk management. As VP, Compliance & Governance at HELUX.ai, he provides CxO/VP-level consulting advice on current technology trends, solutions, and best practices for digital transformation (DT) with a focus on content convergence, process improvement and automation, change and risk management, and governance and compliance. Amitabh participates in the development of standards, certification exams, and writes about DT. Recent contributions are: “Information Governance Body of Knowledge, 1st ed.,” “CIP 2019” updated exam; “Understanding Blockchain’s Role in Trusted Systems;” “ISO/DIS 18759 Document management — Trusted storage sub-system (TSS) functional and technical requirements,” “Starting the Digital Transformation Journey in a Pandemic: Understanding Concepts and Enablers;” and “The Handbook of Archival Practice.” He has presented at ARMA International, ARMA Canada, ARMA chapters, AIIM chapter, PMI OVOC, and SharePoint Saturday conferences. As well, he has hosted a series of webinars on DT. Amitabh is a member of ARMA, PMI, AIIM, a VP and board member of AIIM True North Chapter, the Standards Council of Canada (SCC), and ISO TC 171/SC 2/WG 11 of the International Organization for Standardization (ISO). His certifications include PMP, CIP, and IGP, and he has BCSc. (Honors), MSc. (Comp.Sc.), and MSc. (Proj.Mgmt.) degrees.
 Business Analysis2021.09.27Part 3: OMG! Not another digital transformation article! Is it about effecting risk management and change management?
Business Analysis2021.09.27Part 3: OMG! Not another digital transformation article! Is it about effecting risk management and change management? Business Analysis2021.09.22Part 2: OMG! Not another digital transformation article! Is it about the evolution from RIM to Content Services?
Business Analysis2021.09.22Part 2: OMG! Not another digital transformation article! Is it about the evolution from RIM to Content Services? Business Analysis2021.09.13Part 1: OMG! Not another digital transformation article! Is it about understanding the business drivers?
Business Analysis2021.09.13Part 1: OMG! Not another digital transformation article! Is it about understanding the business drivers?