The Latest

Roadmap to Smarter Records Management with AI
Executive Summary Artificial Intelligence (AI) has the potential to reshape how organizations manage electronic records. From accelerating classification and compliance to identifying risks, AI offers real solutions to modern governance challenges. While the benefits of AI are clear, success depends on how thoughtfully automation is implemented. Organizations need a strategic, actionable roadmap to adopt AI in a way that is transparent, responsible, measurable, and effective. The Promise of LLM and AI Much promise surrounds Large Language Models (LLM) and AI.
Read Article
Rethinking Records: How Smarter Strategies Are Unlocking Space, Security, and Savings for Law Firms
In an industry where every square foot and every second count, paper records are more than a legacy. They are a liability. While many law firms continue to manage sprawling records rooms and offsite storage contracts, a growing number are discovering measurable value, both fiscal and strategic, by embracing smarter digitization strategies. What began as a facilities or compliance challenge has become central to business operations. At the intersection of hybrid work, evolving client expectations, and growing security obligations lies
Read Article
Whitepaper Review: From Rules to Reflex—Transforming Information Governance into a Cultural Value
Written by Jim Merrifield, ARMA Chair and Director of Information Governance and Business Intake at Robinson+Cole Having spent years helping organizations grapple with the realities of information governance (IG), I was drawn to ARMA International’s whitepaper, “From Rules to Reflex: Transforming IG into a Cultural Value,” to see how it tackled our field’s most persistent obstacle: culture. It’s almost a rite of passage in IG to be baffled by how, despite the explosion of data and sophisticated new technologies, our
Read Article
The Gamification of Records Management
Aside from those who are in the field, no one thinks records management is fun. It is the office-equivalent of doing laundry or cleaning out the garage. However, for our organizations, having information owners properly retain or dispose of information can be an issue that has legal, financial, productivity, and publicity consequences. The best policies or retention schedules are only as good as how well they are followed. So how to get information owners to comply? There are carrots and sticks. Sticks being:
Read Article
AI-Driven Government Efficiency Begins with Smart Digitalization
Artificial intelligence (AI) has the potential to transform government operations and help agencies become more efficient, yet many agencies are not equipped to fully harness AI’s capabilities. The main roadblock isn’t poor algorithms–it’s bad data. A recent White House memo found that data readiness and access to quality data were among the most common challenges agencies face when adopting AI. Since AI is only as accurate and effective as the data it learns from, agencies must first focus on properly
Read Article
Certifiable: Crank Up Your Confidence and Career with Complementary Certifications
In the fields of Records and Information Management (RIM) and Information Governance (IG), professionals are faced with a dynamic but increasingly complex landscape. As the volume and variety of data grows exponentially, so too do the challenges and opportunities for those tasked with managing it. In this context, the intersection of professional development and certifications becomes paramount, serving as a compass to guide practitioners through the ever-evolving terrain of RIM. The Significance of Ongoing Professional Growth The RIM and IG
Read Article
Do We Really Mean “Responsibility”?
To make sure a house is sound, we periodically check the foundation for cracks. When we find one, we need to patch it up, because leaving it in place threatens the stability of the entire structure. What if some of the most fundamental statements Information Management (IM) practitioners have been making until now are actually undermining our work? In this article I’m going to challenge two long-standing practices. Brace yourself. First, I recommend that we remove the statement 'Every employee
Read Article
Moving Forward: The Audit, Conversion, and Destruction of 14 Million Paper Documents — A Case Study
A leading global investment firm initiated a project called Digital Forward to facilitate relocating their New York City office and in doing so transitioned to a digital-first workplace, where efficient, searchable digital records would replace paper files. A Project Manager (PM) led a records team to digitize, audit, and manage over 14 million paper documents accumulated over 40 years. This article will provide an overview of this project, including resources, strategies used to capture data and track progress, as well
Read Article
The First 90 Days: A Quick-Start Guide for New Managers
The first 90 days are critical for any new manager. Whether you’ve been promoted internally and are now responsible for overseeing your former peers or have been brought in from outside and need to get up to speed on a new organization, it can be both an exciting and highly stressful time for new managers! You certainly don't want to come out of the door guns blazing and risk upsetting existing staff, but you likely have countless ideas and projects
Read Article
Unlocking Dynamic Records and Information Management
Records and Information Management (RIM) is a business component vital to organizational success, yet it is rarely an organization's top priority. Underpinning RIM practices at an organizational level is imperative to meeting legal requirements for government agencies and businesses in highly regulated industries. Are you doing your annual file plan reviews? If yes, you are in great shape, right? Have you considered that organizations re-organize, information systems become obsolete, others get decommissioned, and regulations change? An annual file plan review
Read Article
Understanding and Documenting the Basis of Retention Periods
The business world is dynamic: people come and go, laws change, and business requirements change, but having a history of why your organization is retaining or deleting a record after a certain period of time will make it more comprehensible to your users, your management and your successors as records managers. A retention schedule is one of the most fundamental aspects of a records management policy. However, the retention periods can often seem arbitrary or obscure. Information owners may wonder
Read Article
The Conundrum of Events-Based Retention Periods
Is Schroedinger’s cat alive or dead? The answer in quantum mechanics is that both are true. Is a record subject to retention or disposition? Again, both can be true at once and no more so than when records are existing within event-based periods. It is clear when a record has a defined time-based retention period such as 5, 10, or 20 years. It becomes more difficult when a disposition is based on an event, such as termination of a contract,
Read Article
Five Obstacles to IG Policy Approval
In the best circumstances, a well-crafted draft IG policy will sail through an approval process like a ship in warm water with strong breezes. Too often, though, the proposed policy hits an iceberg, which stops it in its tracks. At best, there’s little damage and the approval process can continue; at worst, the ship sinks and you head back to the drawing board. Here are five situations that commonly pose obstacles to quick policy approval, and how to get past
Read Article
Staying Ahead of the Curve: 6 Top Legal Tech Trends to Watch in 2023
The legal industry has earned its cautious reputation to “watch and wait” before adopting technology. But forward-looking organizations are increasingly turning to technology to automate processes, streamline operations, enhance customer service and collaboration, increase efficiency, and remain competitive. As technology continues to evolve and become more accessible, law firms need to stay on top of the latest legal tech advancements. In 2023, we see six significant trends that considerably impact the legal industry. These include artificial intelligence (AI), hybrid and
Read Article
Hello. Goodbye… Goodbye. Hello
Why matter mobility management should now be a key competence for law firms Law firms need to get better at matter mobility for two reasons: it’s happening with increased frequency, plus poor matter mobility management can have significant negative impacts on the firm, as Chris Giles explains. Why is there more matter mobility now? Several factors are driving the increase. The first is that ever since 2008, corporate clients are much more cost-conscious and in pursuit of the best available
Read Article
Records Managers—Become the Easy, Adjustable, Reliable Tool of the Organization
Records managers, compliance, finance, information technology, legal, and privacy departments are all concerned with the proper management of information. For records managers, though, their primary focus is the proper management of information. For other functions, proper management of information is a tool used in achieving their objectives, but not necessarily their primary focus. For records managers to work well with compliance, finance, information technology, legal, and privacy departments, the records management department must become an essential tool for those departments.
Read Article
IG Policies: What is Good Content?
“Can anyone share their policy on…?” Hang around the myARMA community long enough and you’ll see this question pop up time and time again. On …retention …data …privacy …security—you name it, and someone has put out feelers to find a policy to use as a template for their own. We all know that even if there is no perfect IG policy, it can be very helpful to look at others’ documents as models for your own. Nevertheless, two points are
Read Article
Four Risk Mitigation Strategies for Effective Project Management
Effective project management requires a proactive approach to mitigating risk. Here are some proven strategies for making sure your projects stay on track. When beginning the planning phase of a project, one of the first things to consider is what can go wrong. This might sound pessimistic, but effective project managers know that a proactive approach to risk management is always better than leaving things to chance. Risks include anything that can potentially impact the performance, budget, timeline, or output
Read Article
The Ethical Use of Artificial Intelligence
Michael Haley, President of ARMA International; Michael Quartararo, President of ACEDS E-Discovery; and George Socha, Senior Vice President of Brand Awareness at Reveal participated in a webinar earlier this year on the ethical use of artificial intelligence. In the webinar, we started with definitions—what do we mean by ethics, AI, machine learning? From there we turned to the impact of AI on today’s world, negative as well as positive. For the bulk of the session, we focused on what could
Read Article
Build and Sustain Your Records Program with a Records Management Playbook
What if your organization’s entire records team won the lottery today and quit? What would happen to your records program? How long would it take your organization to rebuild the team from scratch? If you had a records management playbook in place, your newly hired team could hit the ground running! What is a Playbook? In sports, a playbook describes the “plays” a team executes to accomplish its goals and objectives—generally, winning a game or match. Plays are tailored to
Read Article
Putting the Human back in the Data: Using Data to Lead Change
When you think about data, what is the first thing that comes to mind? Do you love it? Or do you think you’re “not a numbers person”? Do you have concerns about security? Or validity of the data you collect? Or do you think of the technology that you use? Does your mind jump straight to the targets set by the leaders in your organization? And whether or not you’re likely to achieve them? We all have different reactions to
Read Article
Legacy Disposition Program Series: Article Two—Tangible First Steps
This article is a continuation of the Legacy Disposition White Paper article series. Where article one focused on establishing the basics—defining various disposition strategies, highlighting the importance of implementing said strategies in a firm’s IG environment, and walking through the steps leading up to implementation; this article will provide tangible steps for starting a disposition initiative of your very own. Keep in mind that a disposition program is not “one size fits all,” and the steps below (and really, from
Read Article
You Rolled Out Your Remote Workplace in Record Time. Now Let’s Talk Governance
When it comes to the digital workplace, governance and expediency are not always the best of friends. Governance essentially takes a longer-term view, establishing controls, processes and rules that makes the digital workplace sustainable going forward. Expediency tends to yield to the short-term view, cutting corners to drive forwards an immediate need, with the mid- to longer-term view filed under “worry about it later.” Of course, with the COVID-19 crisis, expediency has been the primary concern of most digital workplace
Read Article
The IGP Exam: New and Improved
As the world’s leading membership organization serving professionals who manage and govern information, ARMA is pleased to announce the release of its updated Information Governance Professional (IGP) Certification Exam. As of July 15th, 2022, professionals in information governance, information management, as well as information security, technology, and privacy have access to the new and improved IGP Certification Exam. The IGP is the premier certification focused exclusively on the high-level, strategic practice of information governance. The IGP designation is a requirement
Read Article
Top Information Governance Principles for your Mailroom
Do information governance principles apply to your organization’s mailroom? Mail has typically been a perfunctory function aligned with other physical office services, but for many organizations, the COVID-19 pandemic has shifted mail to a critical—and digital—operation. Mail workflows include sensitive client information, launch new work, and therefore often billable activity. This means matter-centric record creation is starting right from mail delivery, not later from a pile on a desk—even if it is a digital pile on a virtual desk. Protection
Read Article
QC-ing the QC
This article is my advice for a holistic approach to QA/QC for document capture projects. It is also a recommendation to audit the effectiveness of QC methodologies used (or to be used) by a service provider. I tried my best to harness lessons learned and expertise gained during more than half a century in the computer industry, half of which has been focused on digital document capture. I always tried to defy conventional wisdom using creative new methodologies against a
Read Article
Implementing an Archival Display in an in-House Archive
A common misconception is that only financial- and personnel-powerful archives like state and federal archives have the resources to implement an exhibit displaying part of its archival collection. You may think that such an exhibit would not be possible for a small in-house archive team whose primary workflow includes processing, maintaining, and preserving its records and documents. However, you may be surprised what a small or in-house archiving team can accomplish with relatively few resources. Why Implement an Exhibit? Of
Read Article
Data Conversion: Dos and Don’ts
As technology continues to evolve at a rapid rate, it is inevitable that you will be faced with at least one data conversion project during the course of your career. There are many reasons why your organization might face a data conversion project. Your current system may be outdated. Perhaps you are in need of enhanced capabilities that are not supported in your current system. For example, a previous box management system utilized by our office did not support a consistent format for data
Read Article
Chronicle of a Records Manager: Controlling the Chaos of Disaster Response and Recovery
In the field of records management, there are logistical and large-scale projects that can challenge and perplex RIM professionals. These undertakings require planning, communication, documentation, and collaboration to be successful. In some instances, a RIM professional knows a project is imminent and has time to prepare. In other cases, a project may arise unexpectedly, forcing a RIM professional to use the knowledge they have acquired throughout their career forthwith, instead of planning ahead. Some projects may require the advice of
Read Article
The Impact of Data Protection Laws on Your Records Retention Schedule
It is essential that your organization’s records retention schedule is compliant with the data protection requirements in the jurisdictions where your organization operates. This task may seem overwhelming since jurisdictions around the world are enacting new laws, regulations, and requirements; and organizations are continuing to expand their jurisdictional footprint. The purpose of this article is to remove the fear and intimidation of domestic and global data protection laws and show how these laws and requirements are consistent with the existing
Read Article
Records Inventory 101:
101 Just Sounds Good—There is Nothing Basic About a Records Inventory Introduction In records administration, an inventory is a detailed listing of each record/record series or system, along with a location indicator, and other essential data. It is a list of each series or system rather than a list of each document or folder. The primary goal of the inventory is to supply the data needed to create the timetable for the inventory, and it also aids in the detection
Read Article
Defensible Disposition Program: Article One—Let’s get down to Basics
For as long as there has been communication and work, there has been a means of documenting and tracking it. Sales receipts, pay stubs, tax documents, letters, memoranda, and beyond all have value at one time or another. Sometimes, those records need to be revisited or referenced later down the road in connection with, for example, taxes, audits, or other reviews. Not knowing whether something will be needed in the future has led to a cultural mantra of “better to
Read ArticleWhitepaper: Are You Stuck in the Past with Your RIM Program and Software?
by Jasmine Boucher, BMgt, CIP SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION View PDF: Are You Stuck in the Past with Your RIM Program and Software? Back to Sagesse Whitepapers Back to Sagesse 2022 Introduction Many knowledge workers are introduced to records and information management (RIM) as a task that is completed from the side of their desk. Often the reason behind this is due to the lack of an official records management program or dedicated staff
Read ArticleÊtes-Vous sur la Bonne Voie? Un Apercu de la Planification Strategique
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION par Christine Ardern, CRM (retraitée), FAI View PDF: SAGESSE_2022 ETES-VOUS SUR LA BONNE VOIE - UN APERCU DE LA PLANIFICATION STRATEGIQUE_FR Back to Sagesse 2022 Résumé La planification stratégique peut sembler intimidante et rébarbative. Toutefois, les avantages de la planification l’emportent sur les inconvénients et contribuent à créer une feuille de route pour les activités de programme. Dans ce document, nous examinerons les éléments qui constituent la planification
Read ArticleDo You Know Where You are Going? A Look at Strategic Planning
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Christine Ardern, CRM (retired), FAI View PDF: SAGESSE_2022 DO YOU KNOW WHERE YOU ARE GOING A look at Strategic Planning Back to Sagesse 2022 Abstract Strategic planning may seem to be a daunting process and just one more thing to do. The benefits of planning outweigh the time involved and help create a road map for program activities. This paper will look at the elements which go
Read ArticleLa Gestion des Documents et de l’Information est Essentielle au Développement et a l’Impleméntation de Systèmes
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION par Tod Chernikoff, CRM, IGP, CIP View PDF: SAGESSE_2022 LA GESTION DES DOCUMENTS ET DE L’INFORMATION EST ESSENTIELLE AU DÉVELOPPEMENT_FR Back to Sagesse 2022 Résumé Les personnes qui achètent ou conçoivent des systèmes de gestion de l’information n’ont pas toujours en tête la conformité aux exigences en matière de gestion des documents et de l’information. Pour combler cette lacune, le personnel chargé de la gestion des documents et
Read ArticleRecords and Information Management is Vital to System Development and Implementation
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Tod Chernikoff, CRM, IGP, CIP View PDF: SAGESSE_2022 RECORDS AND INFORMATION MANAGEMENT IS VITAL TO SYSTEM DEVELOPMENT AND IMPLEMENTATION rv 1 Back to Sagesse 2022 Abstract There is frequently a gap between those who buy or develop information management systems and compliance with records and information management requirements. To bridge that gap an organization’s records and information management staff must be involved in the Software Development Lifecycle
Read ArticleInformation Governance vs Data Governance: What’s the Difference and Why Does it Matter?
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Jennifer Bodnarchuk, MSc, PhD SAGESSE_2022-INFORMATION GOVERNANCE VS. DATA GOVERNANCE Back to Sagesse 2022 Abstract In this increasingly digital age, the line between data and information is blurred, and for those working to govern and manage data and information, this can add complexity to an already complex task. The thesis of this article is that the distinct differences between data and information do not need to be understood
Read ArticleLe Respect de la Souveraineté des Données des Premières Nations dans le Cadre de la Gestion des Documents et de l’Information
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION par Centre de gouvernance de l’information des Premières Nations View PDF: SAGESSE_2022 LE RESPECT DE LA SOUVERAINETÉ DES DONNÉES DES PREMIÈRES NATIONS DANS LE CADRE DE LA GESTION Back to Sagesse 2022 Résumé L’article commence par la présentation du Centre de gouvernance de l’information des Premières Nations (CGIPN) et de ses travaux. Il définit ensuite les concepts de souveraineté des données des Premières Nations et de données des Premières
Read ArticleRespecting First Nations Data Sovereignty in Records and Information Management
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by The First Nations Information Governance Centre View PDF: SAGESSE_2022 RESPECTING FIRST NATIONS DATA SOVEREIGNTY IN RIM FINAL Back to Sagesse 2022 Abstract The article begins with an introduction to the First Nations Information Governance Centre (FNIGC) and their work. It then defines the concepts of First Nations Data Sovereignty and First Nations data before briefly outlining the First Nations Principles of OCAP®. The paper ends with a
Read ArticleEnhance Communications to Improve Privacy Practices
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Anne-Marie Hayden, Communications & Privacy Consultant, Hayden Public Relations & nNovation LLP View PDF: SAGESSE_2022 ENHANCE COMMUNICATIONS TO IMPROVE PRIVACY PRACTICES Back to Sagesse 2022 Abstract Good communications are vital to organizations proactively meeting their privacy obligations. Certain techniques can also help manage privacy challenges when they inevitably arise. In this article, discover concrete techniques to better comply with consent and openness requirements and improve online privacy
Read ArticleSay Goodbye to May Long Weekend
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Mark Grysiuk, C|CISO, CRM, CIP View PDF: SAGESSE_2022 SAY GOODBYE TO MAY LONG WEEKEND FINAL Back to Sagesse 2022 SAY GOODBYE TO MAY LONG WEEKEND is a fictional case study about a Canadian organization attacked by hackers right before May long weekend. All their core systems go down. The Records Manager plays a critical role in guiding management decisions and providing insights into incident response planning. What
Read ArticleImpact of Tangible Cost Asset (TCA) Accounting on Electronic Recordkeeping Practices
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Bruce Miller, MBA, IGP View PDF: SAGESSE_2022 TCA IMPACT ON RM Back to Sagesse 2022 Introduction The purpose of this report is to document specific changes in recordkeeping practices that will be required for a municipality that has fully implemented TCA (Tangible Capital Asset) accounting practices. The changes in recordkeeping will occur in the following areas: The procedures used to create, identify (label), and file records in
Read ArticleThe Strange Case of Dr. Digitization and Mr. Film: Preservation of Film Records in a Digital Medium
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Oscar Alonso Aguilera Garcia View PDF: SAGESSE_2022 THE STRANGE CASE OF DR. DIGITIZATION AND MR. FILM Back to Sagesse 2022 Abstract Film strip decay is one of the most significant challenges that archivists must confront in the near future. With the renewed interest in and debate surrounding the film preservation in recent years - especially since the adaptation of digital material in the film industry - it
Read ArticleIntroduction
SAGESSE VOLUME VII WINTER 2022 - AN ARMA CANADA PUBLICATION by Barbara Bellamy View PDF: SAGESSE_2022 INTRODUCTION Back to Sagesse 2022 From the Editor Welcome to the seventh edition of Sagesse: Journal of Canadian Records and Information Management, an ARMA Canada publication. We have several great articles written by some familiar authors and first time Sagesse authors for you to enjoy. As always, we welcome your feedback. Sagesse Editorial Team I would like to thank the Editorial Review
Read Article
Part 3: OMG! Not another digital transformation article! Is it about effecting risk management and change management?
Abstract Humans have used technology to transform their societies from prehistoric times up to the present. Society begrudgingly accepted the transformative changes, yet the changes moved society forward. Now information technologies and the information revolution are again transforming society. The COVID-19 pandemic further accelerated the transformation from many years to just a couple of years. This 3-part series discusses digital transformation (DT) from several perspectives. Part 1 discussed the key DT business drivers, concepts, and technology trends, how they are
Read Article
Part 2: OMG! Not another digital transformation article! Is it about the evolution from RIM to Content Services?
Abstract Humans have used technology to transform their societies from prehistoric times up to the present. Society begrudgingly accepted the transformative changes, yet the changes moved society forward. Now information technologies and the information revolution are again transforming society. The COVID-19 pandemic further accelerated the transformation from many years to just a couple of years. This 3-part series will discuss digital transformation (DT) from several perspectives. Part 1 discussed the key DT business drivers, concepts, and technology trends, how they
Read Article
Part 1: OMG! Not another digital transformation article! Is it about understanding the business drivers?
Abstract Humans have used technology to transform their societies from prehistoric times up to the present. Society begrudgingly accepted the transformative changes, yet the changes moved society forward. Now information technologies and the information revolution are again transforming society. The COVID-19 pandemic further accelerated the transformation from many years to just a couple of years. This 3-part series will discuss digital transformation (DT) from several perspectives. Here, Part 1 discusses the key DT business drivers, concepts, and technology trends, how
Read Article
Revisiting Our Views on Non-Compliance with IM Policy
Are we biased when we try to interpret the reasons for non-compliance with information management (IM) policies? Over the past two years, I’ve presented a session titled “Improving Buy-In to IM Policies” to more than a dozen ARMA chapters. We start each session by polling the room to learn who would like to see more buy-in to IM policies at their organizations. Predictably, at least 95% of the participants do. That a large number of us still experience a significant
Read Article
What’s Next in Information Governance? Continuous Audit and Analytics
While it has been said that there is no one-size-fits-all solution for information governance (IG). – What is less often said, but equally valid, is that one-off approaches to IG are no longer recommended. IG cannot be a thing that you do once and then leave alone and expect ongoing success. No, it is ARMA’s suggestion that IG be an ongoing approach, one that is continuously applied and improved over time. While most companies have previously employed point-in-time establishment of
Read ArticleHow Projects, Technology and Solutions Were Impacted By COVID-19: The Issues and Solutions We Faced
SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION by Troy Sawyer View PDF 12-Sagesse-2021-How-Projects-Technology-and-Solutions-Were-Impacted-by-COVID-19 Back to Sagesse 2021 Abstract This article looks at the impact of COVID-19 on various consulting projects in which I was involved and looks at the challenges posed by the shutdown and clients working from home. Introduction As records and information management professionals, we have always worked well offsite with our clients, using tools such as conference calls and remote desktop sharing to develop,
Read ArticleExtraordinary and Pragmatic: Targeted Information Management in Higher Education
SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION by Jay Jorgensen, MLIS CRM View PDF 11-Sagesse-2021-Extraordinary-and-Pragmatic Back to Sagesse 2021 Abstract Higher education institutions are a birthplace for innovation and creativity through teaching, learning and research. Building and implementing pragmatic administrative processes can augment innovation and capabilities by enabling effective and efficient resource allocation and decision-making.This article highlights technology selection, process and information management considerations through case studies that were rapidly implemented at the University of Alberta at
Read ArticleLeveraging Digital Transformation to Benefit Student Learning – Creating a Digital Student Record in Alberta
[vc_row][vc_column][vc_column_text] SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION by Donna Molloy View PDF 10-Sagesse-2021-Leveraging-Digital-Transformation-to-Benefit-Student-Learning pdf Back to Sagesse 2021 Abstract The use of a digital student record is transforming recordkeeping practices for the creation, management, and disposition of student records in Alberta. Student records document decisions that support student learning and their creation is mandated through provincial government legislation. This article identifies what organizations need to consider for digital transformation projects. Specifically, it identifies strategies for Alberta
Read ArticleRepenser le calendrier de conservation : Comment élaborer un calendrier de conservation adapté aux logiciels
[vc_row][vc_column][vc_column_text] SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION par Bruce Miller, MBA, IGP view PDF 09-Sagesse-2021 Re-Envisioning the Retention Schedule FR Back to Sagesse 2021 Abstrait Les logiciels modernes de tenue de documents électroniques offrent de nouvelles capacités et techniques de gestion qui n’étaient pas possibles avec les documents physiques. Ces capacités comprennent notamment les multiples règles de conservation par catégorie, l’attribution de la conservation en fonction de la valeur du document, les multiples déclencheurs
Read ArticleRe-Envisioning the Retention Schedule : How to Build a Software-Ready Retention Schedule
[vc_row][vc_column][vc_column_text] SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION by Bruce Miller, MBA, IGP View PDF 08-Sagesse-2021-Re-Envisioning-the-Retention-Schedule-EN Back to Sagesse 2021 Abstract Modern electronic recordkeeping software provides new capabilities and techniques for managing digital records that were not previously possible with physical records. These capabilities include such things as multiple retention rules per category, retention assignment based on document value, multiple retention triggers and types, retention override, automatic declaration of records, and more. Many of these new capabilities are
Read ArticleMedical Information Management for COVID-19 or Other Medical/Emergency Procedures
[vc_row][vc_column][vc_column_text] Sagesse Winter 2021 - An ARMA Canada Publication by Alexandra (Sandie) Bradley, CRM, FAI 06-Sagesse-2021-Personal-Medical-Information-Management-for-COVID-19-or-Other-Medical-Procedures pdf Back to Sagesse 2021 ABSTRACT This paper will examine why one’s personal medical information is a critical record, why record keeping techniques are necessary to access and preserve this information, and how this information assists with successful medical treatment. Observations are based on the author’s personal journey through the Canadian health care environment. Beyond treatment, a person should also
Read ArticleStarting the Digital Transformation Journey in a Pandemic
SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION By Sandra Bates and Amitabh Srivastav, IGP, CIP, PMP View PDF 05-Sagesse-2021-Starting-the-Digital-Transformation-Journey-in-a-Pandemic-Final Back to Sagesse 2021 Abstract Digital transformation (DT) is a key drive and a critical factor for organizational success in the current digital business environment. The reality of the world-wide pandemic significantly affected normal business and social activities, and has vaulted DT to the forefront of management’s priorities. DT has forced management in businesses and governments alike to digitally transform
Read ArticleThe Current State of Privacy in Canadian Archives
[vc_row][vc_column][vc_column_text] Sagesse Winter 2021 - An ARMA Canada Publication by Madeleine Krucker and Nicole D’AngelaMI Graduates, Faculty of Information, University of Toronto View PDF 04-Sagesse-2021-The-Current-State-of-Privacy-in-Canadian-Archives Back to Sagesse 2021 Abstract This paper explores the situation of privacy in Canadian archives, focusing on personal records within non-government institutions. It provides a review of Canadian privacy legislations and past discussions in the information management community that have addressed the relationship between archives and privacy. Through investigating the
Read ArticleLa Loi sur le droit d’auteur et les droits de propriété intellectuelle autochtones pour les archivistes et les gestionnaires de documents canadiens
SAGESSE WINTER 2021 - AN ARMA CANADA PUBLICATION par Tomoko Shida View PDF 03-Sagesse-2021-Copyright-Law-and-Indigenous-Intellectual-Property-Rights-Final_FR Back to Sagesse 2021 Abstrait Ce document met en lumière les obstacles de la Loi canadienne sur le droit d’auteur au respect des notions autochtones de propriété et de contrôle de la propriété intellectuelle en ce qui concerne les documents destinés ou conservés dans les archives. Il donne d'abord un aperçu de l'évolution des connaissances autochtones et des droits de propriété intellectuelle selon les principes archivistique,
Read ArticleCopyright Law and Indigenous Intellectual Property Rights for Canadian Archivists and Records Managers
Sagesse Winter 2021 - An ARMA Canada Publication By Tomoko Shida 02-Sagesse-2021 Copyright Law and Indigenous Intellectual Property Rights Back to Sagesse 2021 ABSTRACT This paper highlights barriers within Canada’s Copyright Act to respecting Indigenous notions of ownership and control over intellectual property in relation to records destined for or held in archives. It first provides an overview of developments regarding Indigenous knowledge and intellectual property rights in the archival sphere, before turning to the Canadian legal context to examine
Read ArticleIntroduction
Sagesse: Journal of Canadian Records and Information Management an ARMA Canada Publication Winter, 2021 | Volume VI, Issue I View PDF 01-Sagesse-2021-Introduction-to-Sagesse Back to Sagesse 2021 Welcome to ARMA Canada’s sixth issue of Sagesse: Journal of Canadian Records and Information Management, an ARMA Canada publication. Sagesse Editorial Team Sagesse’s Editorial Board wishes to thank Uta Fox, CRM, FAI, for publishing five World Class issues of Sagesse. Uta is one of the founding members of Sagesse as well as the original
Read Article
Which Records Should We Retain in Paper? A Global Guide to Media, Location, and Transfer Compliance
Just tell me which records we must retain in paper! This is a common frustration among records managers and information governance (IG) professionals. Those responsible for maintaining and producing records want to retain or transfer their records using the most efficient method of storage, but do not want to break the law by retaining the information in an illegal format. The purpose of this article is to provide records managers and IG professionals with guidance on determining which records they
Read Article
Information Governance: Alignment with Business is Essential
An optimal IG program is one that aligns with the business processes and strikes the right balance in addressing the value side and the risk side of information. Achieving an ideal alignment between IG and the business is a steep challenge. Commonly, the business stakeholders and end users are more concerned with the immediate availability of information so that work can get done. Few business users are mindful of information risk and compliance requirements. This mindset can lead to friction
Read Article
New Podcast Series Focuses on the Careers of Women Leaders in Information Governance
Launched this July, The Women Leaders in Information Governance podcast series features the career stories of successful women in the IG profession. Lynn Molfetta, Information Governance Strategist | MC Bernstein Data and Katie Tall, Marketing Manager | Nyxeia are the creative force behind and builders of the series. Women leaders in IG in their own right, Molfetta and Tall designed the series to “inspire other women in similar fields to keep moving in a trajectory that shatters the glass ceiling.”
Read Article
What Can We Learn About the IG Profession from the ARMA InfoCon 2020 Taxonomy
Taxonomies can tell us a lot because they’re a reflection of what they organize. Last year, the ARMA team developed a taxonomy to apply to our ARMA InfoCon conference sessions, to make it easier to navigate our myriad of sessions. Since a taxonomy is a reflection of what it organizes, in this case we’re reflecting our profession. We’ve found our ongoing taxonomy development to be incredibly intriguing and informative. Now, many of the terms in our taxonomy represent common themes
Read Article
How the Pandemic Can Affect IG in Positive Ways
We are in the midst of some major societal changes because of this pandemic. Whether you are struggling with staying at home or struggling with having to go to work, one thing is sure — we are all learning new ways to work with the resources we have. I see two big shifts that could impact the way corporations see and leverage information governance (IG): 1) The pandemic has made us more aware of our individual need for privacy and
Read Article
Sanctions for the Loss of Ephemeral Messaging
ARMA is pleased to provide access to an article originally published on BloombergIndustry.com. Just how “ephemeral” are so-called ephemeral messages? In this article, former United States magistrate judge Ronald J. Hedges and Gail Gottehrer explore issues surrounding the potential for spoliation sanctions under Fed. R. Civ. P. 37 (e) for loss of ephemeral messages and lay the foundation for why eDiscovery and information governance best practices need to be extended to address this popular method of communication. Click here to
Read Article
Antiquated Policy Wording: Part 4 — The Problem with “Should”
This is the final article of a four-part series on drafting requirements in IM policies, looking at the problems of using the words “must,” “may,” and “should.” Of the three modal verbs discussed in this article, “should” suffers the worst identity crisis. It is the most versatile of the terms, which really means that it is the most ambiguous. Part 1 Part 2 Part 3 Part 4 In traditional policy wording, writers use “should” to indicate a strong recommendation. Consider
Read Article
Antiquated Policy Wording — Part 3: The Problem with “May”
This is the third article of a four-part series on drafting requirements in IM policies, looking at the problems of using the words “must,” “may,” and “should.” The word “may” suffers from the same deficiencies as “must,” discussed in Part 2. It often creates ambiguity around which element is actually optional. Worse, it masks whether the permission being granted is actually an entitlement, an eligibility, or a discretionary power. Part 1 Part 2 Part 3 Part 4 In traditional policy
Read Article
Antiquated Policy Wording — Part 2: The Problem with “Must”
This is the second article of a four-part series on drafting requirements in IM policies, looking at the problems of using the words “must,” “may,” and “should.”(Read Part 1 here.) In traditional policy wording, writers use “must” to indicate that a requirement is mandatory, for example: Part 1 Part 2 Part 3 Part 4 When the fire alarm rings, employees must exit the building. The word “must” in this statement creates an obligation on one or more people. We can
Read Article
Antiquated Policy Wording: Part 1 — “Must,” “May,” and “Should”
This article is the first of a four-part series on drafting requirements in IM policies, looking at the problems of using the words “must,” “may,” and “should.” Part 1 — Overview The traditional use of “must,” “may,” and “should” when drafting policy requirements is problematic. It’s time to modernize our approach to making rules and drop those terms completely. The conventional approach to indicating the relative strictness of these three words can be summarized as follows: Part 1 Part 2
Read Article
Management of Public Records and FOI: Closing the Gaps in Responsiveness
Records managers around the world are likely familiar with freedom of information (FOI) laws in their respective countries, especially when considered at the national or federal levels. But recent research concerning local, municipal-level compliance with these laws holds important lessons, especially for records managers who work in the public sphere. This new research shows that local compliance with FOI laws is inadequate, subject to manipulation, and influenced by legal and political factors. In the United States, the federal Freedom of
Read Article
What IG Professionals Should Know About the Internet of Bodies
Welcome to the Age of the Internet of Bodies A company in Wisconsin had a “chipping party” in 2017 to implant microchips in some of its employees to make it easier for them to access the buildings and systems and to buy food in the company break room.[1] Those employees joined a growing number of workers in other countries – Belgium, the UK, and Sweden, to name a few – who use microchips for workplace security, convenience, and commuting. Microchips
Read Article
Good Policy Statements Don’t Micro-manage
Instructions in a policy statement that amount to micro-management confuse rather than clarify the requirements. I’m sure you’ve seen them – policy statements so detailed that they list the steps required. Take the following example, excerpted from a real policy (as are the others below): Business areas must set aside time every year to review their classification structure for currency and accuracy. Can you see the micro-management there? The outcome that we want is to receive feedback annually from each
Read Article
Pentagon’s Warning on DNA Testing is Applicable to all Consumers
On December 23, Yahoo News[1] reported on a Department of Defense memo[2] warning military personnel that using direct-to-consumer (DTC) DNA testing could pose “personal and operational risks.” Notably, in its opening paragraph, the missive cites “unintended security consequences and increased risk to the joint force and mission.” In other words, the Pentagon is concerned about hostile entities using such biometric data to better surveil and track the military. Two paragraphs later, this point is made more clearly: “[T]here is increased
Read Article
Introducing the Information Governance Implementation Model (IGIM)
This year, ARMA International released the Information Governance Implementation Model (IGIM), beta version. There are, of course, other information governance (IG) models available to the community, each looking at IG through a different lens. Why should you take the time to look at yet another model? At the highest level: 1) because the IGIM offers an implementation-focused approach that we think many practitioners will find especially useful, and 2) because it will enable you to better use the resources ARMA
Read Article
Cloud, Intelligent Content Services, and Digital Fragility: What’s on the RIM Horizon for 2020
Highlights of the Forrester Research and ARMA International Records Management Online Survey, Q4 2019 2019 marks ten years since ARMA International and Forrester Research first surveyed records and information management (RIM) decision-makers to understand the key trends and challenges facing the profession. Dozens of respondents from around the world shared their perspectives in the survey that ran in September-October 2019. Here is a quick summary of the respondents’ profile: North America once again dominates the survey responses, with U.S. participants
Read Article
Do You Have the Right Stuff to Transition to Information Governance?
In the late 1950s, the United States invited its top test pilots to apply to become the nation’s first astronauts. As memorialized in the book The Right Stuff, test pilots then had to decide whether to transition into an uncertain-yet-vaguely-familiar new career or continue along their present path. Some made the move and became famous; others didn’t, and many of them faded into history. If you are in the records space today, then you are standing at a similar crossroads.
Read Article
The Challenge of Balancing Information Access Demands and Risk Management Throughout the Information Lifecycle
As consumers, we have become accustomed to having information on just about everything available at our fingertips. That expectation has carried over into the workplace, too, where our employees, customers, and business partners alike have an increasing expectation and need for near-instantaneous access to information. Balancing these access needs against the requirements to manage information compliantly and to make sure it does not fall into the wrong hands can be a challenge, and it is a challenge that must be
Read Article
Discovery Dispute Comes to a Head in Theranos Case
A discovery dispute in the criminal prosecution of Elizabeth Holmes and Ramesh Balwani serves as a reminder of the importance and challenge of keeping your e-discovery house in order. It seems even federal prosecutors and agencies sometimes fall short of the mark, too. On November 4, Ethan Barron of Mercury News reported on a discovery dispute between defense attorneys and federal prosecutors concerning the adequacy of the prosecution’s production (“Theranos case: Judge to set hard deadline as lawyers bicker over
Read Article
Have You Considered Tone of Voice?
When we review an old information management policy to see if it needs updating, what do we look for? Too often an organization will revise the operative content but fail to update the tone of voice. Obviously we check for accuracy to make sure the policy statements still reflect the current decisions of the organization, the references are all valid, and so on. We also check for policy alignment to make sure we aren’t repeating statements now found elsewhere. We
Read Article
Summary – “Blockchain Technology and Recordkeeping”
This article summarizes a report published by AIEF on May 30, 2019. Additionally, the article is included in Information Management Magazine, ARMA-AIEF Special Edition, which will be available for download in November. A printed version of the special issue will be available as well, for a nominal fee. Blockchain is often defined as ledgers with entries organized in an append-only, sequential chain using cryptographic links and distributed out and stored on a peer-to-peer computer network. It’s an emerging recordkeeping technology
Read Article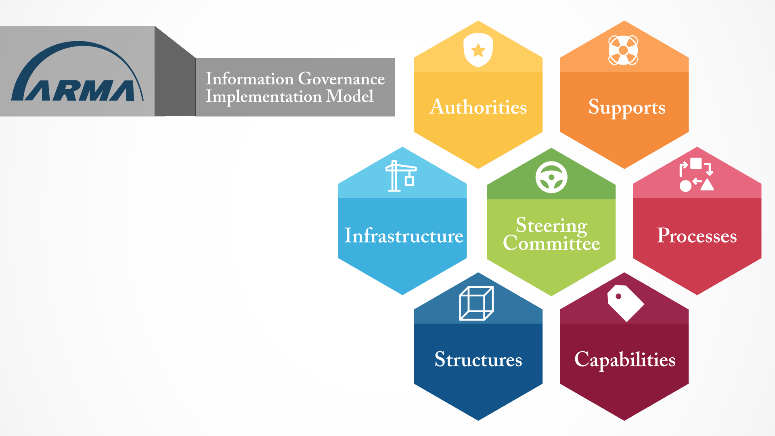
Take the IG Maturity Index Survey
Take the IG Maturity Index Survey Now There is still time to participate in the Information Governance (IG) Maturity Index Project. Does your organization have the necessary elements in place to implement a successful information governance (IG) program? Is your organization leading or falling behind others in your industry? Are there gaps in your IG program? Find out by completing a short survey and help us build the IG Maturity Index. (The survey has eight substantive questions plus a few
Read Article
Documentation Theory for Information Governance
This article is part of a collaboration between ARMA and AIEF and is included in Information Management Magazine, ARMA-AIEF Special Edition, which will be available for download in November. A printed version of the special issue will be available as well, for a nominal fee. Documentation the Emblem of Modern Society? Documentation is a central feature of the contemporary world. We are immersed in documents in nearly every sphere of life and constantly engage with them. Our lives, in many
Read Article
AI, Records, and Accountability
This article is part of a collaboration between ARMA and AIEF and is included in Information Management Magazine, ARMA-AIEF Special Edition, which will be available for download in mid-November. A printed version of the special issue will be available as well, for a nominal fee. Introduction Artificial intelligence (AI) promises wide-ranging benefits for society, but it also poses a host of ethical challenges, such as racial and gender bias, liability for harms caused by AI systems, inequality, economic dislocation, and
Read Article
Summary – “Industry in One: Financial Services”
This article summarizes a report published by AIEF on June 26, 2019. Additionally, the article is included in Information Management Magazine, ARMA-AIEF Special Edition, which will be available for download in mid-November. A printed version of the special issue will be available as well, for a nominal fee. The scope of a records and information management (RIM) program in financial services can seem overwhelming. Compared to other industries, the complexities of managing records and information in financial services are arguably
Read Article
Summary – “Retention of Accounting Records: A Global Survey of Laws and Regulations”
This article summarizes a report published by AIEF on June 3, 2019. Additionally, the article is included in Information Management Magazine, ARMA-AIEF Special Edition, which will be available for download in mid-November. A printed version of the special issue will be available as well, for a nominal fee. This article summarizes the findings of a global survey of legal retention requirements for accounting records, a category of recorded information that is created and maintained by virtually all companies, government agencies,
Read Article
ARMA, AIEF Collaborate for Special Edition of IM Magazine
ARMA International and the ARMA International Educational Foundation (AIEF) are pleased to announce their collaboration on Information Management Magazine, ARMA-AIEF Special Edition, published in mid-November. Download the free PDF format. Purchase in print format. The special edition, which is available for free download or can be purchased in print format, contains summaries of three AIEF-sponsored research reports on the topics of (1) retention of accounting records around the globe; (2) blockchain technology and recordkeeping; and (3) RIM in the financial
Read Article
Anonymization & Pseudonymization as Tools for Cross-Border Discovery Compliance
Introduction Companies that conduct business internationally, and their lawyers, today face a significant challenge balancing U.S. discovery demands against the requirements of Europe’s General Data Protection Regulation (GDPR). Most U.S. courts and investigators expect parties that are involved in litigation or investigations to comply with requests for potentially relevant documents in their possession, custody, or control, regardless of whether the documents are located within or outside the United States. However, the data privacy and data protection rules of many countries
Read Article
Sponsored Content: Microfilm in The Digital World
Bringing the best technology to the full life cycle of microfilm, e-ImageData’s ScanPro® line of microfilm scanners moves you into the digital world with speed and economy. Today, in this digital age, users expect information to be easily and quickly accessible. Information on microfilm is no exception. So, it is no surprise that the focus today is to convert those trillions of stored microfilm records to a digital format to make it possible to quickly locate the information and immediately
Read Article
New Cohasset/ARMA Benchmarking Report Says ‘We Aren’t There Yet’
ARMA International and Cohasset Associates are excited to announce the 2019 Information Governance Benchmarking Report. In 1999, Cohasset Associates launched the survey, which has tracked the evolution of the information profession over the past two decades. In that time, more than 14,000 respondents have helped chronicle the evolution to information governance (IG). On its title page, the newly released edition of the Information Governance Benchmarking Report asks this question: “Are we there yet?” The answer, according to Carol Stainbrook, executive
Read Article
Eisen’s Book on Rule-Writing Delivers on its ‘How-To’ Promises
Usually I pick up a how-to book only if it’s in the way of a book I want to read, but Lewis S. Eisen’s How to Write Rules That People Want to Follow (Pixley Press) conquered my bias rather quickly. Here are four reasons I’d recommend the book to anyone in the workplace: First, the topic is fresh and pertinent. Few would argue against his view that rules too often sound crabby and aggressive and are frequently unclear. In the
Read Article
Will Google Play Fair in the ‘Privacy Sandbox?’
On August 22, Justin Schuh, a director on Google’s Chrome Engineering team, introduced the company’s plans for a “privacy sandbox,” a colorful title for its initiative that purports to strengthen web privacy. The news appeared on Google’s blog in an article titled “Building a more private web.” According to Schuh, the need for a privacy sandbox stems from certain data practices that “don’t match up to user expectations for privacy.” He suggests that when other browsers allow the blocking of
Read Article
Can Information Management Policies Be Both Clear and Concise?
Most information management (IM) professionals would agree that well-written policies are clear and concise. Too often, though, the policies are “dumbed down” because someone is afraid that maybe, somewhere, some individual in the organization might not be familiar with one of the technical words used in the policy. The logic is that if one person doesn’t understand the policy as worded, that lack of understanding would be a terrible thing. The result of such caution is either (1) a policy
Read Article
Managing Legacy Paper Files in the Digital Era
Addressing your organization’s legacy paper files and capturing them in your digital information ecosystem may feel like a daunting task. As discussed in our recent white paper, capture is the first step in the information lifecycle and is essential for achieving digital transformation and enabling the strategic alignment of information activities envisioned by information governance (IG). Paper files are effectively “dark,” inaccessible to your organization’s digital information ecosystem until they are captured through scanning, either imaging or digitization.1 Download the
Read Article
Sorting Through the Whirlwind of News on the Proposed Equifax Settlement and Capital One Breach
On July 22, 2019, the Federal Trade Commission (FTC) announced that it had reached a proposed settlement with Equifax in connection with a 2017 data breach that exposed sensitive, personal data of around 147 million people. According to the FTC’s press release, the data breach included “names and dates of birth, Social Security numbers, physical addresses, and other personal information that could lead to identity theft and fraud.” (See FTC press release Equifax to Pay $575 Million as Part of
Read Article
Concerns Over FaceApp Remind Us That Users May Not Fathom the Permissions They Grant Apps
Geoffrey A. Fowler, tech columnist for the Washington Post, opens his July 17 article with a question that’s pertinent to millions of app users: “When an app goes viral, how can you know whether it’s all good fun — or covertly violating your privacy by, say, sending your face to the Russian government?” In an email response, the founder of Russian-based FaceApp answers Fowler’s question: Yaroslav Goncharov asserts user data is not transferred to Russia. But should Russian servers even
Read Article
A Pair of Foundational Concepts
The following is an excerpt from the ARMA Guide to the Information Profession. Words matter and word choices matter. In any profession that is looking to move forward in maturity, there are often vernacular issues that make gaining a comprehensive understanding of the profession a challenge. This is one of the reasons bodies of knowledge are so incredibly helpful: they help to clarify the vocabulary of a profession. The information profession is filled with confusing terms, misused terms, and confusing
Read Article
Goals of New Canadian Digital Charter Include Assuring Privacy, Eradicating Hate Online
Multiple news outlets are reporting on Canada’s new digital charter, which comprises 10 principles that are based on Canadian values that should guide all future government policies, legislation, and programs. When introducing the charter late last month, Navdeep Bains, minister of Innovation, Science, and Economic Development, emphasized that data will drive business in the new digital economy. But he also noted that privacy, security, and “trust” are fundamental priorities, suggesting that Canadians must be able to trust their information is
Read Article
Why Are Businesses Opting for Edge, AI, and IoT – and Are They Wise to Do So?
Edge computing is increasingly associated with at least two “trending” terms in the IT and information arenas: Internet of Things (IoT) and artificial intelligence (AI). Broadly speaking, the term refers to computing that’s done at or near the source of the data. Today, a great percentage of data is stored in the cloud and may therefore be located continents away. These great distances can result in delays in computing, which can impact an organization’s capacity to optimally analyze and leverage
Read Article
Attorneys Respond to Delaware Court’s Affirmation That Emails and Texts May Constitute Corporate Books and Records
In reporting on recent actions in the Delaware courts, WilmerHale attorneys Stephanie C. Evans and Alan J. Wilson remind organizations to carefully manage all evidence of communications among boards and directors, whether it comes in traditional formats or through less formal media. Writing for Mondaq, the attorneys note that several court actions this year in Delaware have clarified the scope of the Delaware General Corporation Law, Section 220, which gives stockholders and directors the right to demand access to an
Read Article
IG Exec Has Learned From Failures, Says IG Success Requires C-Suite Presence
Aaron Bryant, chief IG officer at the Washington State Department of Health, recently provided CIODive.com with an account of the lessons he’s learned in his 14 years as a leader of IG programs and the keys to finding IG success. Bryant, also a faculty member of the Compliance, Governance, and Oversight Council (CGOC), concedes that most information pros know by now that IG success relies on close coordination among stakeholders, but he warns that “operationalizing this can be challenging.” Too
Read Article
Judge’s Ruling May Provide Clues to the Outcome of Employee’s ‘Dropbox’ Privacy Suit
Earlier this year, a judge from the Western District of Pennsylvania acted on behalf of employee privacy rights when she partially denied a public employer’s motion to dismiss a suit that accused it of violating the plaintiff’s Fourth Amendment rights. As summarized on Mondaq.com, Elizabeth Frankhouser, an employee of an educational facility, used her personal Dropbox account to store personal and workplace data. Hence, a link to Dropbox was on her workplace screen, though no data contained in the account
Read Article
As it Nears its First Anniversary, the GDPR Gets Predictably Varied Reviews
Later this month, the EU’s General Data Protection Regulation (GDPR) will mark its one-year anniversary, and multiple news outlets are chiming in with commentary on the impact of the landmark law. Legaltechnews, for instance, reports on an IAPP Global Privacy Summit session in which a European data protection official and others reviewed the law’s first year and forecasted what might come next. Among her comments, Andrea Jelinek, the European Data Protection Board chair and Austrian Data Protection Authority director, noted
Read Article
How to Break the Mold of Negativity Around IM Policies
Most people associate IM policies with notions like requirements and restrictions. Those connotations are unfortunate because that’s not what writing rules is about. Written properly, rules are primarily about getting clarity and about target setting. No matter what the field — IM, IT, Security — rules are about helping people do the right thing. The negative connotations are understandable, though, given the tone of voice of many policy documents. Often organizations claim to hold “respect for others” as a core
Read Article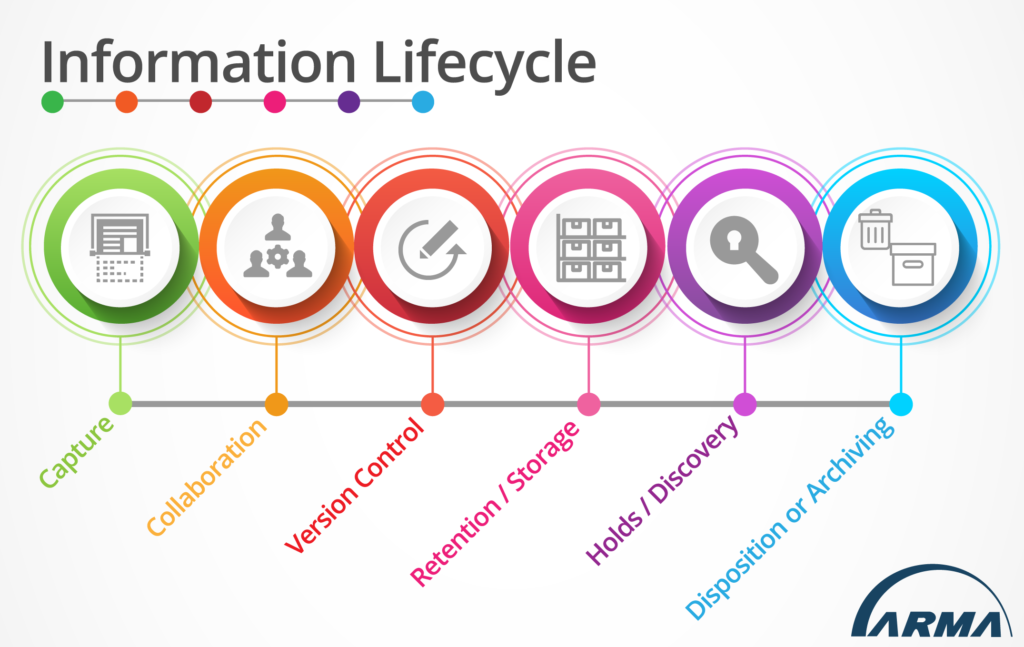
Mapping Document Management Processes (Leveraging an Information Lifecycle)
(The following is an excerpt from an ARMA White Paper "Reviving Document Management: How the Knowledge and Experience of Document Management Can be Leveraged for Organizational Improvement", sponsored by Access.) Processes around documents must mirror the processes around all organizational information. A consistent lifecycle for all information in an organization must be applied, with room for the unique nuances of document management to assert themselves. For this consistency across systems and classes of information (including documents), one should leverage an
Read Article
Establishing a Collaboration Process to Bolster Knowledge Management
Collaboration: interacting with peers and colleagues to exchange ideas, share experiences, work together on projects, and solve problems. Work teams, project teams, and communities need a consistent way to share their knowledge, coordinate their activities, and communicate with one another. Providing a process for collaboration enables basic functions such as document and photo libraries, file sharing, membership rosters, lists, discussions, polls and surveys, calendars, meeting sites, and links. Making this process a standard ensures that there is a consistent way
Read Article
Mind Tools for Managers: A Crash Course in Effective Management Skills
Mind Tools for Managers: 100 Ways to Be a Better Boss focuses on identifying the complete list of skills that managers can master to be better leaders in their organizations. The authors provide working professionals with practical advice for these competencies – such as the ability to adequately cope with change and stress – and they direct their readers to an accompanying website where they can access such external resources as videos, skill-building articles, and worksheets. Key topics from this
Read Article
ARMA Q&A: GDPR Regulations and Electronic Records
Question: "What are the GDPR regulations for personal data in electronic records such as social media, video, and instant messages?" Answer: Since May 28, 2018, the General Data Protection Regulation (EU) (2016/679) (GDPR) has been in force. The GDPR is not new; it is an updated replacement for the now repealed Data Protection Directive (1995/46/EC). Article 3 of the GDPR states that it applies to the processing of personal data by a controller or a processor, whether inside or outside
Read Article
Utah to Become Leader in Digital Privacy
The Utah legislature just passed landmark legislation in support of a privacy law that protects private electronic data stored with third parties (like Google and Facebook) from free-range government access. Molly Davis, in an opinion piece on Wired.com, applauds the move: “Prosecutors and law enforcement may argue they need the power of data collection to protect the public from potential criminals. But individual liberty protections are far more important than perceived safety risks. If there is a legitimate safety concern
Read Article
‘Alexa, Fix My Records!’ A Look at AI in the Information Profession
To many people, “artificial intelligence” is a bit of an oxymoron. It is the suggestion that we can create something that then can be creative on its own. If intelligence is the ability to acquire and apply knowledge and skills, requiring a measure of judgement and reasoning, can we create such a thing through mechanical or digital means? Some scholars suggest that artificial intelligence (AI) isn’t intelligence at all, but rather an advanced machine skill-set that is mathematically driven and
Read Article
The Next Internet: Will it Serve the Public’s Interest?
The Next Internet has arrived. The Internet of previous years has been replaced by a new iteration that is profoundly changing the digital landscape. In Becoming Digital: Toward a Post-Internet Society, Vincent Mosco introduces the Next Internet by analyzing the three pillar technological systems that constitute it, namely cloud computing, big data analytics, and the Internet of things. The central argument is that these three pillar technological systems “comprise an increasingly integrated system that is accelerating the decline of a
Read Article
Migrating Legacy Records – a Case Study
Organizations that maintain electronic records systems may at some point need to undertake either a records conversion or migration to address software obsolescence. This article discusses how the Calgary Police Service’s (CPS) records and information management (RIM) and information technology (IT) teams collaborated to ensure that nearly four million criminal case file records stored in its legacy system – a system used for more than 40 years – were successfully migrated to a new, off-the-shelf records management system (RMS). Migrating
Read Article
ARMA President-Elect Says Expanded California Privacy Bill ‘Ups the Ante’ for IG
California Attorney General Xavier Becerra endorsed a bill last week that expands the state's new privacy act to permit consumers to sue companies over their handling of personal data. The privacy law that was passed in 2018 gave consumers the right to sue only in the case of a data breach. The new bill allows them to sue over any violations. Becerra acted against the wishes of tech lobbyists, according to Reuters. Jason Stearns, ARMA’s president-elect, says the expansion of
Read Article
Beyond Compliance: Eight Steps for Using Privacy By Design to Develop a Privacy Program
Governments globally are passing strict information privacy laws and regulations, and organizations are being hard-pressed to comply with them or suffer stiff penalties. Using the principles of Privacy By Design, organizations can design a privacy program to meet this challenge. Mandatory privacy breach reporting. Privacy impact assessments. Access to information requests. The right to be forgotten. If these terms, which pop up in regulations like the European Union’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act, and Canada’s
Read Article
Why Information Architecture is Vital to Information Governance
Whether you are migrating petabytes of content from an obsolete enterprise content management (ECM) platform to a modern content management system (CMS) or just looking to make your intranet less awful, it’s time to get started with information architecture (IA). You know that information volumes, varieties, and velocities are ever increasing in today’s fast-paced digital world. This has created a growing urgency in not only managing all our content and data, but in actually governing it. Organizations need to intelligently
Read Article
Professionals in Data Collection and Management Will Find Value in New Edition of ‘Fundamentals’
Reviewed by Ana Rosa Blue TITLE: Fundamentals of Collection Development and Management, Fourth EditionAuthor: Peggy JohnsonPublisher: ALA EditionsDate: 2018Length: 432 pagesPrice: $85.00 | ALA Members: $76.50ISBN: 13 978-0-8389-1641-4 (softcover)Source: ALA Store Peggy Johnson describes her book Fundamentals of Collection Development and Management (fourth edition) as “a comprehensive introduction for students, a primer for experienced librarians with new collection development and management responsibilities, and a handy reference resource for practitioners as they go about their day-to-day work.” Indeed, those tasked with
Read Article
Master Leader or Master Servant?
Fellows Forum Starting with his role as a team captain on the football field, Dave McDermott set out to become a good leader. From that experience, his father, workplace mentors, and an enlightening book he learned that a successful leader has to serve those he is leading, being willing to “pick up a broom and sweep floors right along the side of the people he or she is responsible for.” Many, many years ago I was fortunate enough to be
Read Article
Isaza Responds to Illinois Supreme Court Ruling on Biometric Privacy
In January, the Illinois Supreme Court ruled an individual does not have to plead an actual injury or harm, apart from the statutory violation itself, in order to sue under the Illinois Biometric Information Privacy Act (BIPA), as reported by Jeffrey Neuburger of Proskauer. The long-awaited decision stems from Rosenbach v. Six Flags Entertainment Corp. According to Neuberger’s account, because the BIPA statute does not define “aggrieved,” many legal arguments and amicus briefs have tried to influence the Court as
Read Article
Legalweek 2019 Kicks Off With Former United States Attorneys General Loretta Lynch and Alberto Gonzalez Focused On Cybersecurity
Two former U.S. Attorneys General helped kick off Legalweek 2019 by sharing their thoughts on such pressing issues as cybersecurity, privacy, civil rights, and more. Former attorneys general Albert Gonzalez and Loretta Lynch spoke frankly in a discussion attended primarily by attorneys and moderated by ALM’s Molly Miller. (ARMA International, a track sponsor of Legalweek 2019, was represented in the audience as well.) Miller, the chief content officer for ALM, asked Gonzalez and Lynch to describe what the U.S. government
Read Article
Dropbox Buys Hello Sign, Adds its Coveted Workflow Capabilities
Dropbox has announced its acquisition of HelloSign, an organization that provides document workflow and e-signature services. Whitney Bouck, COO of HelloSign, told ARMA International that the company is “thrilled to be joining the Dropbox family.” She said, “With so many similarities between our products, business models, and cultures, it’s a natural fit. This move will accelerate our mission to give customers a better way to get work done.” Quentin Clark, Dropbox’s senior vice president of engineering, told TechCrunch that the
Read Article
Google Is Fined $57 Million, First Major Penalty Under Europe’s Data Privacy Law
The New York Times was among the many sources recently reporting that the French data protection authority fined Google about $57 million for “not properly disclosing to users how data is collected across its services – including its search engine, Google Maps and You Tube – to present personalized advertisements.” It’s the largest penalty given for violating the General Data Protection Regulation (GDPR). According to the Times, it “shows that regulators are following through on a pledge to use the
Read Article
Stuck in Rewind? Dynamic E-Discovery for Cloud Data
An array of new cloud-based digital sources has emerged across the corporate landscape: chat tools, collaboration platforms, cloud productivity suites, and more. Programs like Slack, Office 365, and Salesforce bring many new and exotic challenges to corporations trying to organize, control, and produce data from these programs, and e-discovery can be particularly daunting when wrestling with the unique characteristics of this data. In many cloud-based platforms, documents are saved approximately every 30 seconds to ensure that the user’s working data
Read Article
Information Governance Body of Knowledge Published
Published on Oct. 22, the Information Governance Body of Knowledge (IGBOK) provides information governance (IG) stakeholders – information management, information technology, legal, risk/compliance, privacy, security, and business unit heads – the clear, concise, and practical guidance they need to govern their organization’s information assets effectively. Filled with strategic advice, policy guidance, “how to” processes, and valuable templates, IGBOK was developed by a group of subject matter experts representing the IG stakeholder groups; collectively, this group has more than 500 years
Read ArticleAssociation News: Fellows, Britt Literary, Other Winners Named at ARMA Live! 2018
The following award winners for the last fiscal year (July 1, 2017, to June 30, 2018) were announced at ARMA International’s 63rd Annual Conference & Expo in Anaheim, California, in mid-October. Company of Fellows ARMA International’s highest recognition is to be named to its Company of Fellows. This award honors ARMA members who have distinguished themselves through outstanding achievements and contributions in information management, as well as through noteworthy accomplishments in all levels of the association. This year’s two inductees
Read Article
To Improve Your Information Systems, You Must Understand the Architecture
Information Systems: Process and PracticeEditors: Christine Urquhart, Faten Hamad, Dina Tbaishat, and Alison YeomanPublisher: Facet PublishingPublication Date: December 2017Length: 288 pagesPrice: $89ISBN: 978-1783302413 In Information Systems: Process and Practice, Christine Urquhart and a group of highly respected researchers study the concept of information architecture (IA) within information systems (IS) management. The book explores how IA can help library science and other information professionals meet the challenges of today’s technology-driven world and capitalize on the power of data management. Two Areas
Read Article
New Edition on Metadata Use Provides ‘Tutorial’
Metadata for Information Management and Retrieval: Understanding Metadata and its Uses, 2nd ed.Authors: David HaynesPublisher: Facet PublishingPublication Date: 2018Length: 288 pagesPrice: $69ISBN: : 978-I-85604-824-8Source: alastore.ala.org As part of my activities as a records manager and archivist, I regularly collect and create metadata without articulating my philosophy about doing so or possessing great expertise in either activity. This book encourages reflection on how and why we use metadata. It is aimed at information professionals in museums, libraries, and archives, as well as
Read Article
U.S. Seeks a New Start to Talks on Global Cybersecurity Practices
Cyberscoop.com reports that at the recent United Nations (U.N.) session, White House officials gauged interest in restarting talks on global cybersecurity norms. Such negotiations crumbled in 2017 because of acrimony among certain countries, reportedly due to disagreements between Washington and Moscow and others over the right to self-defense in cyberspace. In a recent meeting with agents from some 20 U.N. countries, U.S. Deputy Secretary of State John J. Sullivan encouraged renewing the conversation at the U.N. Group of Governmental Experts
Read Article
Proposed NAFTA Replacement Recognizes Need For Privacy Framework
Recently the United States, Mexico, and Canada proposed a new trade pact to replace the North American Free Trade Agreement (NAFTA). According to the HuntonPrivacyBlog, the new pact recognizes “the economic and social benefits of protecting the personal information of users of digital trade” and will require the three nations to “adopt or maintain a legal framework that provides for the protection of the personal information of the users[.]” This framework, according to the Hunton blog, should include such principles
Read Article
Wendy’s Sued for Mismanagement of Employee Fingerprints
As reported by ZDNet.com, a class-action lawsuit has been filed in Illinois that claims Wendy’s restaurant chain has broken state laws by improperly storing and managing employee fingerprints. The complaint centers on Wendy’s practice of using biometric clocks that scan fingerprints when employees arrive at work, when they leave, and when they use the point-of-sale and cash register systems. The suit contends that Wendy’s breaks the Illinois Biometric Information Privacy Act (BIPA) because the company doesn’t inform its employees how
Read Article
California Consumer Privacy Act Is Work in Progress, Says Attorney
In a recent piece on Information-Management.com, Matthew Nelson, an attorney with DiscoverReady LLC, says the 2018 California Consumer Privacy Act (CCPA) is constantly evolving, evidenced by the September passing of Senate Bill 1121, which serves rather like an amendment to the CCPA. Nelson says because of SB-1121, consumers bringing a private right of action no longer must notify the attorney general. Further, organizations no longer must disclose on their website or in their online privacy policy that a consumer has
Read Article
Q&A: Fingerprint Security
Question: With fingerprint security technology now used in so many businesses for secured door access, what category does it fall under (e.g., personally identifiable information)? How is the data deleted upon employee termination? Answer: Fingerprint information falls under a type of record referred to as biometrics. These questions bring up several facets of biometric recordkeeping: use, retention, and governance. Biometric Information Uses In addition to being used for secured door access, fingerprints are used routinely in the workplace for timeclock
Read Article
Big Bucket Retention: Objectives, Issues, Outcomes
Fifteen years after its introduction by the U.S. National Archives and Records Administration as a strategy for improving federal agencies recordkeeping performance, the big bucket approach to record retention is in common use. This article summarizes an interview-based study of the objectives, issues, and outcomes of current big bucket retention initiatives in 14 organizations. The study was conceptualized and underwritten by the ARMA International Educational Foundation, www.armaedfoundation.org A traditional retention schedule provides a detailed enumeration – sometimes described as a
Read Article
Blockchain Redux – Cracking the Code on Cryptocurrencies
This article focuses on a facet of blockchain – cryptocurrencies – which are also known as virtual currencies, crypto coins, digital assets, or digital coins. In the November/December 2017 issue of Information Management, author Victoria L. Lemieux provided a SWOT analysis of blockchain recordkeeping, a groundbreaking electronic ledger technology. Deployed for decentralized, secure recordkeeping, its uses continue to be explored and include purposes such as health care, (e.g., electronic medical records), government records management (e.g., deed recording,), and legal services
Read Article
Lost in the Clouds: Liability for Personal Information Breaches
This article summarizes several U.S. Court decisions regarding liability in breaches of personal information collected by third-party service providers on the behalf of other organizations. This is just one aspect of a study of information management-related cases that was solicited by the ARMA International Educational Foundation and underwritten by the ARMA Metro New York City Chapter; it is available at armaedfoundation.org. Organizations have a penchant for capturing increasingly large amounts of information and storing it in distributed systems (i.e., computer
Read Article
Report Says Healthcare Insiders Pose Greatest Data Security Threat
A Verizon report suggests that nearly 60% of data security incidents at healthcare organizations are caused by insiders, according to an article on Law.com. The “Protected Health Information Data Breach Report” implies that healthcare is the only industry in which internal players are the greatest threat to an organization’s data security. The study reviewed 1,368 security incidents involving patient medical records in 27 countries. It included confirmed breaches and security incidents in which data was at risk but not confirmed
Read Article
Norway Plans 1,000-Year Digital Archive for Everything
ZDNet.com reports that near the Arctic Circle, experts at the National Library of Norway’s (NLN) secure storage facility are implementing an astonishing plan for digitizing everything ever published in Norway: books, newspapers, manuscripts, posters, photos, movies, broadcasts, and maps, as well as all websites on the Norwegian domain. The work was begun 12 years ago and will likely take 30 years to complete. According to the article, the library has more than 540,000 books and 2 million newspapers in its
Read Article
Canadian Government Is Improving its Cybersecurity
Eweek.com reports that the government of Canada is taking an active, aggressive strategy to defends its networks from cyber attacks. In October, Scott Jones, head of the Canadian Centre for Cyber Security at the Canadian Security Establishment (CSE), summarized the steps being taken and how individuals and organizations can benefit from the same approach. “Every day, the CSE blocks hundreds of millions of malicious activities directed at the government of Canada... We decided to break the cycle and make it
Read Article
Facebook Says Breach Affected About 50 Million Accounts
As widely reported, the mid-September Facebook data breach may have affected nearly 50 million accounts. Bloomberg.com refers to it as “the latest in a series of missteps that are undermining confidence in the company’s social network and business model.” In a statement, Facebook said it has fixed the breach, which had let hackers take over accounts. The accounts of Chief Executive Officer Mark Zuckerberg and Chief Operating Officer Sheryl Sandberg were among those targeted by the hack, according to Bloomberg.
Read Article
Gartner Foresees the End of On-Premises ECMs in 2019
A recent Gartner Inc. report predicts the current enterprise content management (ECM) market will “devolve into purpose-built, cloud-based content solutions and solution services applications.” According to an article on idm.net.au, the Gartner study finds that organizations are increasingly adopting cloud solutions rather than on-premises ECMs. Software as a service (SaaS) remains the biggest segment of the cloud market, with global revenue predicted to grow 17.8% to reach $85.1 billion in 2019. “The increasing adoption of SaaS applications and other cloud
Read Article
New California Laws Ask IoT Makers for Security Features
California Gov. Jerry Brown has signed two bills that are designed to make manufacturers of Internet-connected devices more responsible for ensuring the privacy and security of Californians, as reported on GovTech.com. The bills require manufacturers to equip connected devices with a “reasonable security feature or features” that are appropriate to their nature, function, and the information they may collect, contain, or transmit. The security features must be designed to protect the device and its information from “unauthorized access, destruction, use,
Read Article
GDPR Invites Collaboration, E-Discovery Panel Says
As reported on Law.com, analysts and attorneys specializing in e-discovery recently suggested the EU’s General Data Protection Regulation (GDPR) may be worth embracing largely because it encourages collaboration among stakeholders and provides an opportunity to embed privacy into the discovery process. That was the view of some panelists in a session titled “International e-Discovery and Data Protection,” held at Relativity Fest 2018, an annual event that focuses on issues in legal discovery. “Eighteen months ago, there seemed to be a
Read Article
Sedona Conference® Explores GDPR Impact on E-Discovery
Law.com reports on a web seminar hosted by The Sedona Conference® international electronic information management, discovery and disclosure working group, which looked at how e-discovery professionals and courts are subject to the EU General Data Protection Regulation (GDPR). Importantly, the panel suggested that the wide scope of what the GDPR considers to be personally identifiable information makes it probable that any EU data collection conducted by U.S. attorneys would have to comply to GDPR standards. In the data-gathering phase at
Read Article
Report Finds Big Increase in Cyber Attacks, Reveals 5 Top Methods
TechRepublic.com cites a recent report from a security company that suggests cyber attacks continue to increase in occurrence. The report, from Positive Technologies, says that the second quarter of 2018 saw a 47% increase in cyber attacks when compared to the same period in 2017. Targeted attacks outnumbered mass campaigns, which indicates a growing sophistication among the cybercrooks. Increasingly, data theft is driving the attacks, with many criminals seeking personal data (30%), credentials (22%), and payment card information (15%). Hackers
Read Article
ACLU Counsel Says Be Wary of Federal Privacy Legislation
In a Washington Post op-ed piece, Neema Singh Guliani, senior legislative counsel at the American Civil Liberties Union (ACLU), warns that the growing push for federal privacy legislation is bad news for consumers. Guliani cites several examples of how states are leading the efforts to protect consumer privacy, including California’s recent consumer privacy act and the Illinois law that sets limits on the commercial collection and storage of biometric data. According to Guliani, the U.S. Chamber of Commerce and lobbying
Read Article
How the Pandemic Can Affect IG in Positive Ways
We are in the midst of some major societal changes because of this pandemic. Whether you are struggling with staying at home or struggling with having to go to work, one thing is sure — we are all learning new ways to work with the resources we have. I see two big shifts that could impact the way corporations see and leverage information governance (IG): 1) The pandemic has made us more aware of our individual need for privacy and protection, and therefore more responsive to others’ needs. 2) The pandemic has pushed the growth of video communications and therefore

Sanctions for the Loss of Ephemeral Messaging
ARMA is pleased to provide access to an article originally published on BloombergIndustry.com. Just how “ephemeral” are so-called ephemeral messages? In this article, former United States magistrate judge Ronald J. Hedges and Gail Gottehrer explore issues surrounding the potential for spoliation sanctions under Fed. R. Civ. P. 37 (e) for loss of ephemeral messages and lay the foundation for why eDiscovery and information governance best practices need to be extended to address this popular method of communication. Click here to read Reproduced with permission. Published June 9, 2020. Copyright 2020 by The Bureau of National Affairs, Inc. (800-372-1033) http://www.bloombergindustry.com. About

Cloud, Intelligent Content Services, and Digital Fragility: What’s on the RIM Horizon for 2020
Highlights of the Forrester Research and ARMA International Records Management Online Survey, Q4 2019 2019 marks ten years since ARMA International and Forrester Research first surveyed records and information management (RIM) decision-makers to understand the key trends and challenges facing the profession. Dozens of respondents from around the world shared their perspectives in the survey that ran in September-October 2019. Here is a quick summary of the respondents’ profile: North America once again dominates the survey responses, with U.S. participants at 77% and Canada at 17%.Government topped the list of vertical industries at 23%.Large enterprise – over $1 billion in

ARMA, AIEF Collaborate for Special Edition of IM Magazine
ARMA International and the ARMA International Educational Foundation (AIEF) are pleased to announce their collaboration on Information Management Magazine, ARMA-AIEF Special Edition, published in mid-November. Download the free PDF format. Purchase in print format. The special edition, which is available for free download or can be purchased in print format, contains summaries of three AIEF-sponsored research reports on the topics of (1) retention of accounting records around the globe; (2) blockchain technology and recordkeeping; and (3) RIM in the financial industry. Full reports can be downloaded from the AIEF site. The special edition also includes two additional articles: one on

Will Google Play Fair in the ‘Privacy Sandbox?’
On August 22, Justin Schuh, a director on Google’s Chrome Engineering team, introduced the company’s plans for a “privacy sandbox,” a colorful title for its initiative that purports to strengthen web privacy. The news appeared on Google’s blog in an article titled “Building a more private web.” According to Schuh, the need for a privacy sandbox stems from certain data practices that “don’t match up to user expectations for privacy.” He suggests that when other browsers allow the blocking of cookies, it actually undermines privacy “by encouraging opaque techniques such as fingerprinting.” The fingerprinting technique consists of developers harvesting small

Sorting Through the Whirlwind of News on the Proposed Equifax Settlement and Capital One Breach
On July 22, 2019, the Federal Trade Commission (FTC) announced that it had reached a proposed settlement with Equifax in connection with a 2017 data breach that exposed sensitive, personal data of around 147 million people. According to the FTC’s press release, the data breach included “names and dates of birth, Social Security numbers, physical addresses, and other personal information that could lead to identity theft and fraud.” (See FTC press release Equifax to Pay $575 Million as Part of Settlement with FTC, CFPB, and States Related to 2017 Data Breach, July 22, 2019.) Equifax agreed to pay between $575

Concerns Over FaceApp Remind Us That Users May Not Fathom the Permissions They Grant Apps
Geoffrey A. Fowler, tech columnist for the Washington Post, opens his July 17 article with a question that’s pertinent to millions of app users: “When an app goes viral, how can you know whether it’s all good fun — or covertly violating your privacy by, say, sending your face to the Russian government?” In an email response, the founder of Russian-based FaceApp answers Fowler’s question: Yaroslav Goncharov asserts user data is not transferred to Russia. But should Russian servers even be our chief concern? Fowler’s article opens with a focus on that issue – including a link to an article

Attorneys Respond to Delaware Court’s Affirmation That Emails and Texts May Constitute Corporate Books and Records
In reporting on recent actions in the Delaware courts, WilmerHale attorneys Stephanie C. Evans and Alan J. Wilson remind organizations to carefully manage all evidence of communications among boards and directors, whether it comes in traditional formats or through less formal media. Writing for Mondaq, the attorneys note that several court actions this year in Delaware have clarified the scope of the Delaware General Corporation Law, Section 220, which gives stockholders and directors the right to demand access to an organization’s books and records “where a proper purpose can be demonstrated.” Importantly, the courts have affirmed that emails, text messages,

Utah to Become Leader in Digital Privacy
The Utah legislature just passed landmark legislation in support of a privacy law that protects private electronic data stored with third parties (like Google and Facebook) from free-range government access. Molly Davis, in an opinion piece on Wired.com, applauds the move: “Prosecutors and law enforcement may argue they need the power of data collection to protect the public from potential criminals. But individual liberty protections are far more important than perceived safety risks. If there is a legitimate safety concern requiring access to a person's data, law enforcement will still be able to obtain a warrant. Without that warrant requirement

ARMA President-Elect Says Expanded California Privacy Bill ‘Ups the Ante’ for IG
California Attorney General Xavier Becerra endorsed a bill last week that expands the state's new privacy act to permit consumers to sue companies over their handling of personal data. The privacy law that was passed in 2018 gave consumers the right to sue only in the case of a data breach. The new bill allows them to sue over any violations. Becerra acted against the wishes of tech lobbyists, according to Reuters. Jason Stearns, ARMA’s president-elect, says the expansion of “the most significant change in the U.S. privacy landscape” heightens the need for a strong IG program within organizations. “This

Isaza Responds to Illinois Supreme Court Ruling on Biometric Privacy
In January, the Illinois Supreme Court ruled an individual does not have to plead an actual injury or harm, apart from the statutory violation itself, in order to sue under the Illinois Biometric Information Privacy Act (BIPA), as reported by Jeffrey Neuburger of Proskauer. The long-awaited decision stems from Rosenbach v. Six Flags Entertainment Corp. According to Neuberger’s account, because the BIPA statute does not define “aggrieved,” many legal arguments and amicus briefs have tried to influence the Court as to its meaning. John J. Isaza, Esq, of Rimon P.C., tells ARMA International the issue is not necessarily settled: “Despite

Dropbox Buys Hello Sign, Adds its Coveted Workflow Capabilities
Dropbox has announced its acquisition of HelloSign, an organization that provides document workflow and e-signature services. Whitney Bouck, COO of HelloSign, told ARMA International that the company is “thrilled to be joining the Dropbox family.” She said, “With so many similarities between our products, business models, and cultures, it’s a natural fit. This move will accelerate our mission to give customers a better way to get work done.” Quentin Clark, Dropbox’s senior vice president of engineering, told TechCrunch that the workflow capabilities were integral to the acquisition: “What is unique about HelloSign is that the investment they’ve made in APIs

Google Is Fined $57 Million, First Major Penalty Under Europe’s Data Privacy Law
The New York Times was among the many sources recently reporting that the French data protection authority fined Google about $57 million for “not properly disclosing to users how data is collected across its services – including its search engine, Google Maps and You Tube – to present personalized advertisements.” It’s the largest penalty given for violating the General Data Protection Regulation (GDPR). According to the Times, it “shows that regulators are following through on a pledge to use the rules to push back against internet companies whose businesses depend on collecting data.” The ruling hits at Google’s basic practice

Information Governance Body of Knowledge Published
Published on Oct. 22, the Information Governance Body of Knowledge (IGBOK) provides information governance (IG) stakeholders – information management, information technology, legal, risk/compliance, privacy, security, and business unit heads – the clear, concise, and practical guidance they need to govern their organization’s information assets effectively. Filled with strategic advice, policy guidance, “how to” processes, and valuable templates, IGBOK was developed by a group of subject matter experts representing the IG stakeholder groups; collectively, this group has more than 500 years of experience and expertise. Those who purchase this edition of IGBOK will receive the second edition free of charge. Learn
Association News: Fellows, Britt Literary, Other Winners Named at ARMA Live! 2018
The following award winners for the last fiscal year (July 1, 2017, to June 30, 2018) were announced at ARMA International’s 63rd Annual Conference & Expo in Anaheim, California, in mid-October. Company of Fellows ARMA International’s highest recognition is to be named to its Company of Fellows. This award honors ARMA members who have distinguished themselves through outstanding achievements and contributions in information management, as well as through noteworthy accomplishments in all levels of the association. This year’s two inductees bring the total number of Fellows of ARMA International (FAIs) to 60. Anita P. Castora, IGP, CRM, CBCP, FAI #59

U.S. Seeks a New Start to Talks on Global Cybersecurity Practices
Cyberscoop.com reports that at the recent United Nations (U.N.) session, White House officials gauged interest in restarting talks on global cybersecurity norms. Such negotiations crumbled in 2017 because of acrimony among certain countries, reportedly due to disagreements between Washington and Moscow and others over the right to self-defense in cyberspace. In a recent meeting with agents from some 20 U.N. countries, U.S. Deputy Secretary of State John J. Sullivan encouraged renewing the conversation at the U.N. Group of Governmental Experts (GGE), according to a U.S. State Department statement. “[N]onbinding norms of responsible behavior during peacetime provides important guidance to states,

Proposed NAFTA Replacement Recognizes Need For Privacy Framework
Recently the United States, Mexico, and Canada proposed a new trade pact to replace the North American Free Trade Agreement (NAFTA). According to the HuntonPrivacyBlog, the new pact recognizes “the economic and social benefits of protecting the personal information of users of digital trade” and will require the three nations to “adopt or maintain a legal framework that provides for the protection of the personal information of the users[.]” This framework, according to the Hunton blog, should include such principles as limitations on collection, choice, data quality, purpose specification, use limitation, security safeguards, transparency, individual participation, and accountability. The agreement

Wendy’s Sued for Mismanagement of Employee Fingerprints
As reported by ZDNet.com, a class-action lawsuit has been filed in Illinois that claims Wendy’s restaurant chain has broken state laws by improperly storing and managing employee fingerprints. The complaint centers on Wendy’s practice of using biometric clocks that scan fingerprints when employees arrive at work, when they leave, and when they use the point-of-sale and cash register systems. The suit contends that Wendy’s breaks the Illinois Biometric Information Privacy Act (BIPA) because the company doesn’t inform its employees how it uses their data and fails to obtain a written release with their explicit consent to obtain and handle the

California Consumer Privacy Act Is Work in Progress, Says Attorney
In a recent piece on Information-Management.com, Matthew Nelson, an attorney with DiscoverReady LLC, says the 2018 California Consumer Privacy Act (CCPA) is constantly evolving, evidenced by the September passing of Senate Bill 1121, which serves rather like an amendment to the CCPA. Nelson says because of SB-1121, consumers bringing a private right of action no longer must notify the attorney general. Further, organizations no longer must disclose on their website or in their online privacy policy that a consumer has the right to delete personal information. Importantly, SB-1121 also made the CCPA effective immediately, but it extended the compliance deadline,

Report Says Healthcare Insiders Pose Greatest Data Security Threat
A Verizon report suggests that nearly 60% of data security incidents at healthcare organizations are caused by insiders, according to an article on Law.com. The “Protected Health Information Data Breach Report” implies that healthcare is the only industry in which internal players are the greatest threat to an organization’s data security. The study reviewed 1,368 security incidents involving patient medical records in 27 countries. It included confirmed breaches and security incidents in which data was at risk but not confirmed as having been compromised. Reporter Kristen Rasmussen says employers may take comfort in knowing that not all the internal breaches

Norway Plans 1,000-Year Digital Archive for Everything
ZDNet.com reports that near the Arctic Circle, experts at the National Library of Norway’s (NLN) secure storage facility are implementing an astonishing plan for digitizing everything ever published in Norway: books, newspapers, manuscripts, posters, photos, movies, broadcasts, and maps, as well as all websites on the Norwegian domain. The work was begun 12 years ago and will likely take 30 years to complete. According to the article, the library has more than 540,000 books and 2 million newspapers in its archive. Because the materials have been mass-scanned and OCR-processed, their content is free-text searchable.NLN’s mandates are for long-term safe storage

Canadian Government Is Improving its Cybersecurity
Eweek.com reports that the government of Canada is taking an active, aggressive strategy to defends its networks from cyber attacks. In October, Scott Jones, head of the Canadian Centre for Cyber Security at the Canadian Security Establishment (CSE), summarized the steps being taken and how individuals and organizations can benefit from the same approach. “Every day, the CSE blocks hundreds of millions of malicious activities directed at the government of Canada... We decided to break the cycle and make it harder for people to discover our vulnerabilities,” he said in a keynote. Jones says the CSE is making it more

Facebook Says Breach Affected About 50 Million Accounts
As widely reported, the mid-September Facebook data breach may have affected nearly 50 million accounts. Bloomberg.com refers to it as “the latest in a series of missteps that are undermining confidence in the company’s social network and business model.” In a statement, Facebook said it has fixed the breach, which had let hackers take over accounts. The accounts of Chief Executive Officer Mark Zuckerberg and Chief Operating Officer Sheryl Sandberg were among those targeted by the hack, according to Bloomberg. Because of user data leaks, security breaches, and the spread of misinformation, Facebook has had to confront hostile congressional hearings

Gartner Foresees the End of On-Premises ECMs in 2019
A recent Gartner Inc. report predicts the current enterprise content management (ECM) market will “devolve into purpose-built, cloud-based content solutions and solution services applications.” According to an article on idm.net.au, the Gartner study finds that organizations are increasingly adopting cloud solutions rather than on-premises ECMs. Software as a service (SaaS) remains the biggest segment of the cloud market, with global revenue predicted to grow 17.8% to reach $85.1 billion in 2019. “The increasing adoption of SaaS applications and other cloud services impacts the management, dissemination and exploitation of enterprise content,” said Craig Roth, research vice president at Gartner. While SaaS

New California Laws Ask IoT Makers for Security Features
California Gov. Jerry Brown has signed two bills that are designed to make manufacturers of Internet-connected devices more responsible for ensuring the privacy and security of Californians, as reported on GovTech.com. The bills require manufacturers to equip connected devices with a “reasonable security feature or features” that are appropriate to their nature, function, and the information they may collect, contain, or transmit. The security features must be designed to protect the device and its information from “unauthorized access, destruction, use, modification or disclosure.” The laws define a connected device as one with an Internet protocol (IP) or Bluetooth address that

Sedona Conference® Explores GDPR Impact on E-Discovery
Law.com reports on a web seminar hosted by The Sedona Conference® international electronic information management, discovery and disclosure working group, which looked at how e-discovery professionals and courts are subject to the EU General Data Protection Regulation (GDPR). Importantly, the panel suggested that the wide scope of what the GDPR considers to be personally identifiable information makes it probable that any EU data collection conducted by U.S. attorneys would have to comply to GDPR standards. In the data-gathering phase at pretrial, bulk collection would not be advisable because counsel must comply with GDPR protocol even when merely transferring data to

Report Finds Big Increase in Cyber Attacks, Reveals 5 Top Methods
TechRepublic.com cites a recent report from a security company that suggests cyber attacks continue to increase in occurrence. The report, from Positive Technologies, says that the second quarter of 2018 saw a 47% increase in cyber attacks when compared to the same period in 2017. Targeted attacks outnumbered mass campaigns, which indicates a growing sophistication among the cybercrooks. Increasingly, data theft is driving the attacks, with many criminals seeking personal data (30%), credentials (22%), and payment card information (15%). Hackers are compromising online platforms, e-commerce sites, online ticketing systems, and hotel booking sites, according to the report. “Cyber-attacks in Q2

ACLU Counsel Says Be Wary of Federal Privacy Legislation
In a Washington Post op-ed piece, Neema Singh Guliani, senior legislative counsel at the American Civil Liberties Union (ACLU), warns that the growing push for federal privacy legislation is bad news for consumers. Guliani cites several examples of how states are leading the efforts to protect consumer privacy, including California’s recent consumer privacy act and the Illinois law that sets limits on the commercial collection and storage of biometric data. According to Guliani, the U.S. Chamber of Commerce and lobbying organizations that represent Amazon, Airbnb, Google, Microsoft, and many other digital behemoths are urging Congress to adopt a federal privacy
News & Analysis
For over 50 years, the ARMA Magazine has been your trusted source of professional knowledge.
ARMA International’s ARMA Magazine and its’ predecessors (Information Management Magazine, Information Management Journal, and ARMA Journal) have been sharing best practices and the experiences of trusted professionals in the information space. Now, we’re making ARMA Magazine more accessible to you, providing you with the knowledge you need, in your browser and on the go.
© 2019 ARMA International

